In this article
Let’s be real, running a business is hard enough without having to worry about cyber attacks. But in a world where threats are always changing, being ahead of the curve isn’t just smart, it’s necessary.
Every day we hear about companies getting hit by cyber attacks, their reputation damaged and their finances strained. But what if you could see these threats coming? What if you had a way to prepare, to harden your defenses before the storm hits?
That’s where Cyber Threat Intelligence (CTI) comes in. It’s not just another buzzword or a fancy tool, it’s a whole new way of thinking about cyber security. CTI is about being armed with knowledge, about understanding the threats that are out there and how they might impact your business so you can pro-actively prepare for them.
The Digital Threat Landscape
Imagine you’re running a small bakery.
You have your recipes locked away, your kitchen is clean and tidy and your doors are locked at night.
But in the digital world it’s as if your bakery exists in a neighbourhood where the landscape changes every day. New alleys appear out of nowhere, filled with shady characters. The locks on your doors might have become obsolete because someone invented a new kind of lockpick.
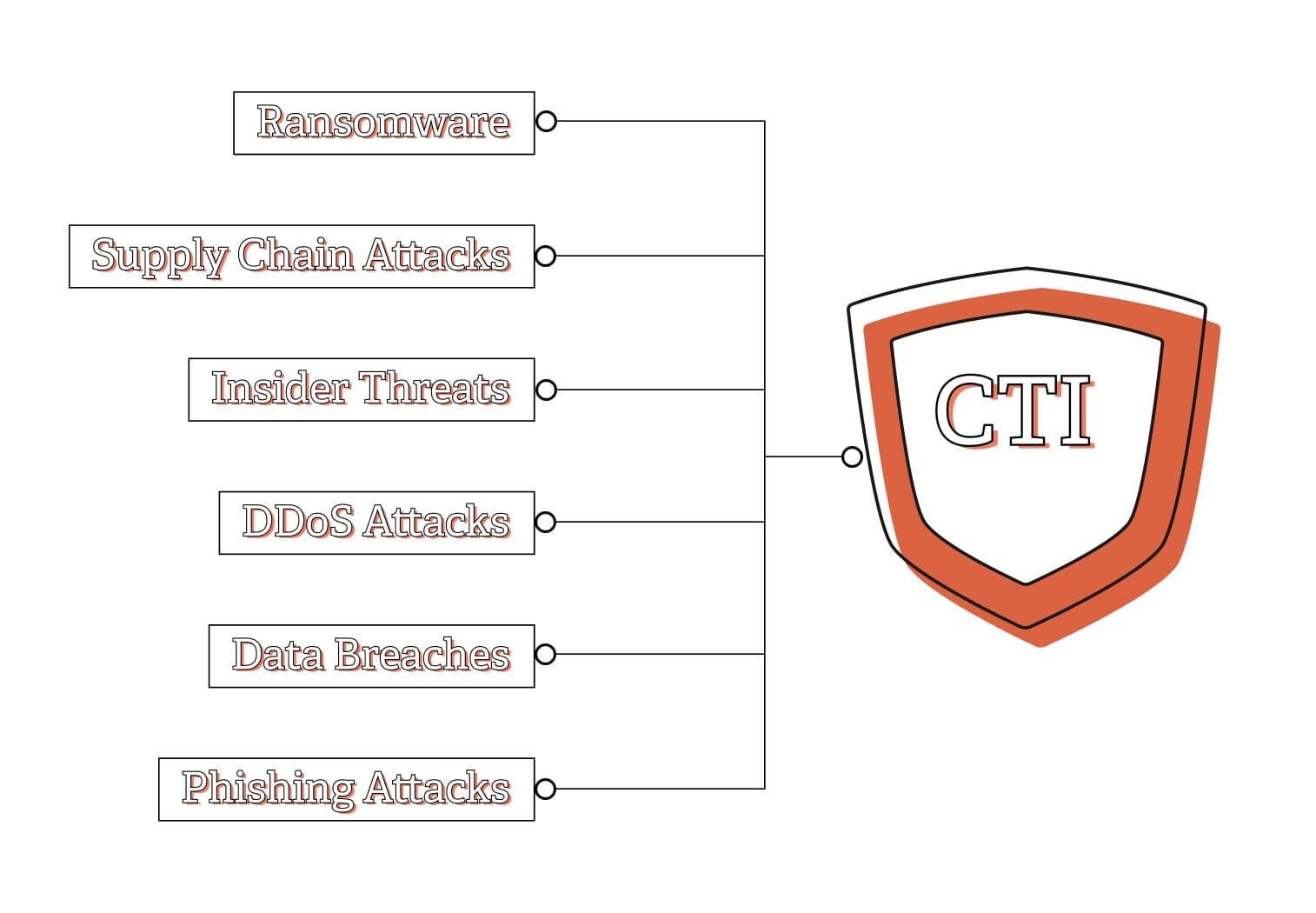
This ever changing, often dangerous digital neighbourhood is what we call the cyber threat landscape. It’s populated by different types of threats, each with their own MO, so cyber security is essential to protect against these evolving threats.
Ransomware: Digital burglars breaking into your shop, locking you out and demanding payment to get back in.
Phishing attacks: Sneaky con artists trying to trick you into handing over your most valuable possessions.
Data breaches: Thieves breaking into your filing cabinet and stealing confidential documents.
DDoS attacks: A massive crowd blocking your shop entrance, preventing genuine customers from getting in.
Insider threats: Realising the threat is from someone in your own shop, a scenario we never expect.
Supply chain attacks: When the weak link isn’t in your chain but your supplier’s.
Why CTI Matters to Your Business
So how do you stay resilient and safe against these threats? That’s where cyber threat analysis and CTI comes in. Cyber threat analysis is key to continuously monitoring files to detect threats throughout their lifecycle.
- See threats before they happen. CTI gives you insight into potential threats so you can anticipate future attacks by understanding the adversary’s tactics, techniques and procedures.
- Make informed decisions about your cyber spend. CTI helps businesses prepare for future threats by analysing long term trends and risks in the cyber landscape.
- Respond quickly when incidents happen by enabling your security teams to act on real-time threat intelligence.
- Protect your reputation and customer trust.
What is Cyber Threat Intelligence
Cyber threat intelligence is the process of gathering, processing, and analysing information about potential cyber threats to help organisations understand and mitigate risk. Cyber threat intelligence, including strategic threat intelligence, is crucial for identifying and mitigating potential threats by analysing various factors, such as the dark web environment and specific attack campaigns, to inform better decision-making and bolster overall security strategies.
It’s about knowing your enemy, their motivations, capabilities, and tactics so you can defend against them. You need to understand the threat actor’s motivations, whether political influence or financial gain, to understand their tactics, techniques, and procedures (TTPs).
CTI vs Traditional Cyber Security
Let’s look at traditional cyber security as if we were building a fortress. You’re right to be focused on a robust home defence, build the walls, setup checkpoints and patrol the perimeter.
But how do you know what treats are coming? CTI are the scouts that give you the data and intelligence about potential attacks so you can prepare and adapt your defences in advance.
From a business perspective, the difference can be distilled down to:
Approach: Traditional (reactive) vs CTI (proactive)
Scope: Traditional (internal focus) vs CTI (wider threat landscape)
Outcome: Traditional (prevention and detection) vs CTI (informed decision making).
The CTI Ecosystem
The CTI ecosystem is a complex network of interconnected components working together to gather, share and leverage threat intelligence. It includes intelligence sources, CTI providers and analysts, tools and platforms, consumers of intelligence and collaborative networks for sharing threat information.
- Intelligence sources (open-source, dark web, proprietary feeds)
- CTI providers and analysts
- Tools and platforms for data processing and analysis
- Threat intelligence platforms collect and collate threat data from multiple sources, to aggregate, analyse and disseminate insights.
- Consumers of intelligence (businesses, government agencies)
- Collaborative networks for threat sharing
CTI Components
Cyber Threat Intelligence (CTI) operates at three levels, each serving a different purpose in strengthening your organisation’s cyber security. By understanding these components you can develop a strategy that covers both immediate threats and long term risks.
Strategic Intelligence: The Overview
Strategic intelligence is the big picture. It looks at long term trends, emerging threats and geopolitical factors that impact cyber risk. This level of intelligence informs high level decision making and long term security strategy.
Example: How escalating geopolitical tensions will lead to more cyber attacks in your industry.
Operational Intelligence: The Short Term
Operational threat intelligence fills the gap between strategic insight and day-to-day security operations. It looks at threats that will emerge in the next few weeks or months, specific vulnerabilities, or attack methods that are gaining traction.
Example: A new type of malware targeting businesses in your sector so you can harden defenses before it hits.
Tactical Intelligence: The Immediate Threat
Tactical threat intelligence deals with the here and now. It provides real-time information on active threats, specific indicators of compromise, and actionable data for response.
Example: A list of IP addresses for an active phishing campaign so you can block and mitigate immediately.
By using all three levels of CTI you can develop a layered defence strategy that’s proactive to the changing cyber threat landscape. So you’re ready for today’s threats and tomorrow’s risks.
Business Benefits of CTI
CTI lets you prepare for threats, moving from reactive to proactive cyber posture. By understanding emerging threats and attack patterns you can harden your defences before an attack happens.
Informed Decision Making
With CTI you have the context to make smart decisions about your cyber security spend. It helps you know which threats are most likely to impact your business so you can prioritise resources.
Quicker Response
When an attack happens CTI can speed up your response and effectiveness. With knowledge of the threat actor’s tactics and techniques your team can quickly identify, contain and mitigate.
Better Resource Allocation
CTI lets you focus on the threats that matter most to your business. This targeted approach means your cyber security resources (human and technology) are used most effectively, where it matters most.
Compliance
By staying ahead of the threat curve CTI can help you maintain compliance with data protection regulations. It lets you anticipate potential weaknesses and fix them before they become compliance issues.
CTI Tools and Technologies
To do CTI you need a suite of specialist tools and technologies. These work together to give you a view of the threat landscape and enable proactive security.
Threat Intelligence Platforms (TIPs)
Are the foundation of a CTI programme. These platforms collect, analyse and distribute threat data from multiple sources. TIPs aggregate and correlate the data to give a single view of the threats. They often have collaboration features so teams can share and coordinate.
Security Information and Event Management (SIEM)
SIEM systems take threat intelligence data and operationalise it. SIEM tools collect and analyse log data from across the organisation’s IT estate, correlating this internal data with external threat intelligence. This correlation helps you identify security incidents faster and more accurately.
Automated Threat Feeds
Provide a continuous stream of threat indicators, such as malicious IP addresses, domains or file hashes. These feeds can be fed into firewalls, intrusion detection systems and other security tools to block or flag potential threats. The real time nature of these feeds means you can update your defences in real time.
Dark Web Monitoring Tools
Are specialist services that scan the dark web for threats specific to your business. These tools can give you early warning of planned attacks, leaked credentials or stolen data being traded on dark web forums. This proactive approach means you can take action before a threat happens. Learn more about dark web monitoring.
By combining these tools you can build a CTI ecosystem that strengthens your overall security posture and keep you ahead of the threat.
The CTI Process
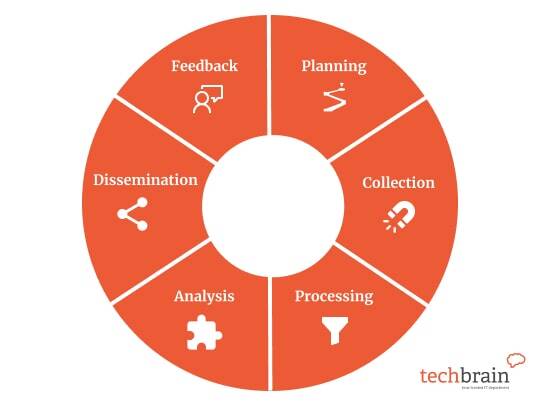
The Cyber Threat Intelligence (CTI) process is a continuous cycle that’s essential to a CTI programme. This six step cycle keeps you responsive to the changing threat landscape:
Planning and Direction
Set the foundation by identifying your key assets, vulnerabilities and specific intelligence requirements. Decide which threats are most likely to impact your business and what you need to protect against them.
Collection
Collect raw data from multiple sources, open-source intelligence, dark web monitoring, proprietary threat feeds, internal logs and information sharing platforms. Cast a wide net to get a view of all potential threats.
Processing
Clean, normalise and structure the data. This means deduplicate the information, translate the data into a common format, add context to the data and filter out the irrelevant or low quality data.
Analysis
Turn data into intelligence. Identify patterns and trends, assess the credibility and severity of the threats, determine relevance to your business, provide context about the threat actors, their motivations and tactics.
Dissemination
Get the intelligence to the right people at the right time. Tailor reports for different audiences, deliver critical information in a timely manner, use the right communication channels and integrate intelligence into existing security tools and processes.
Feedback
Improve your CTI programme by getting feedback from intelligence consumers, measure the impact on security outcomes, identify gaps in coverage and refine collection sources and analytical methods based on real world results.
By following this process organisations can build a strong, adaptive CTI programme that delivers timely, relevant and actionable intelligence to strengthen their overall security posture. CTI is not a linear process but a cycle of continuous improvement.
CTI Implementation Challenges
Building a Cyber Threat Intelligence (CTI) programme is a big challenge. It’s a journey with many obstacles but one that can pay big dividends if done right.
The first hurdle many organisations face is the volume of threat data. It’s easy to feel overwhelmed, drowning in a sea of information. The key is to prioritise quality over quantity. Focus on the intelligence that’s most relevant to your business. Automated filtering tools can help with this, so your team can focus on the threats that matter most.
Resource constraints are another big challenge. CTI requires technological investment and skilled people which can stretch tight budgets. A smart approach is to start small and scale up or work with a CTI service provider. Start with a focused initiative, maybe on a specific type of threat or a critical asset. As you show value you can make a stronger case for more resources.
Integrating CTI with existing security infrastructure is key but complex. Before you start, assess your current security environment thoroughly. This will help you choose CTI tools that fit with your existing systems. Develop a clear roadmap for integration and address potential compatibility issues early on.
The biggest challenge is getting the intelligence to action. Develop clear processes and playbooks for responding to different types of threat intelligence. These should be living documents, reviewed and updated regularly. Create a culture of proactive cyber security within your organisation where teams feel empowered to act on new intelligence.
By tackling these challenges with persistence and strategy you can build a CTI programme that strengthens your security and delivers value to your whole organisation.
Getting Started With CTI
So you’re ready to get started then?
Good move, implementing a Cyber Threat Intelligence (CTI) program is a big step up from being reactive to being proactive in your cyber security.
You’re now on a path that will enable your organisation to stay ahead of threats, make informed decisions and protect your business assets better.
While it may seem overwhelming at first, a well planned approach can make all the difference.
- Set Your Objectives: Define your CTI goals, whether it’s improving threat detection or risk management.
- Start Small, Think Big: Start with a focused approach, like a specific threat feed, then expand out.
- Contextualise for Your Business: Make sure the intelligence you gather is relevant to your industry and risk profile.
- Get Cross-Departmental Buy In: Involve all relevant departments, from IT to executive leadership, for a holistic approach.
- Automate: Use tools to manage and analyse large volumes of threat data.
- Continuously Evaluate and Refine: Regularly review and refine your CTI processes to keep up with the threat landscape.
By following these steps, you’ll be well on your way to building a robust CTI program that enhances your overall cyber security strategy and provides lasting value to your organisation.
Predict, Prevent, Protect your Business
In a world where threats are always changing, cyber threat intelligence isn’t a nice to have – it’s a must have. It’s part of a modern cyber security strategy so you can move from reactive to proactive.
By doing CTI you’re not just protecting your data or your systems – you’re protecting your business’s future. You’re giving yourself the ability to predict, make informed decisions and stay one step ahead of the ever changing cyber security landscape.
Going to the next level of your cyber security journey can seem scary but you don’t have to do it alone. At TechBrain we help businesses like yours strengthen their cyber security with CTI services.
Remember in the world of cyber security knowledge is power.
Your cyber fortress might be robustly defended, but are you proactively on-watch for threats, or asleep at the ramparts?