In this article
Imagine this, you’re sipping your flat white on a Tuesday afternoon, when an email pops into your inbox.
It’s from your CEO. She’s away on business. The subject line says: “Urgent: Invoice Payment Request—Today!” It’s addressed to you, mentions a project your team has been working on, and has a hint of urgency. Your gut says something’s not right, but the email looks legit.
Is it really her, or have you become the latest spear phishing victim?
Cybercriminals have upped their game, trading in clumsy scams for highly targeted, laser guided attacks. Known as spear phishing, these cyber cons focus on specific individuals or roles within an organisation, making it far easier to get past your defences.
Australians aren’t immune; in fact our local businesses and government institutions are very much in the firing line. If you want to protect your business, read on. We’ll explain what spear phishing is, show you real world spear phishing email examples, and give you expert tips to prevent and explore the trends beneath the surface.
Additionally, we will discuss strategies to prevent spear phishing attacks, emphasising the importance of a multifaceted approach that includes security awareness training, technical measures, and continuous education.
Spear Phishing, A Quick Definition
Spear phishing definition refers to a targeted form of phishing that involves sending malicious communications to specific individuals or organisations. While “regular” phishing is like casting a wide net—sending out generic emails hoping someone, somewhere will click, spear phishing is more like choosing a single fish from the barrel.
Attackers research their chosen target. They might look up their target on LinkedIn, scan industry announcements, or even the company’s own about page. Armed with this information, they craft emails that look like they come from a trusted source: a colleague, manager or well known supplier.
The end goal? To trick you into revealing sensitive information, transferring money or downloading malware.
Spear Phishing is on the Rise
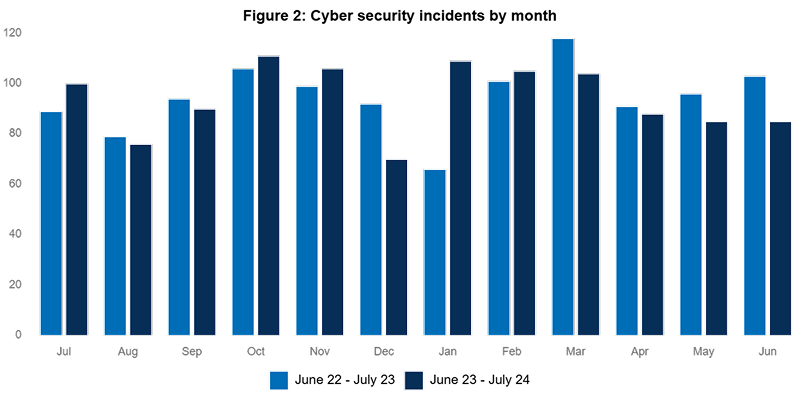
Spear phishing statistics show the prevalence and impact of these attacks, despite being a small percentage of all emails, they account for a big chunk of data breaches, with many businesses getting multiple targeted attacks a day.
The Australian Cyber Security Centre (ACSC) has noted the increase in highly targeted email scams against Australian businesses. In the ACSC most recent annual cyber threat report FY2023-24, the total self-reported business email compromise (BEC) losses to ReportCyber was almost $84 million.
There were over 1,400 reports of BEC made to law enforcement through ReportCyber that led to a financial loss, and on average, the financial loss from each confirmed BEC incident was over $55,000.
Since many high profile breaches start with an employee clicking on just one malicious email, it’s no surprise a big chunk of successful cyber attacks come from spear phishing. Educating employees to stop spear phishing attacks by highlighting the techniques used by attackers and using practical training methods, such as phishing simulations, can significantly enhance awareness and recognition of potential threats.
How Spear Phishing Works
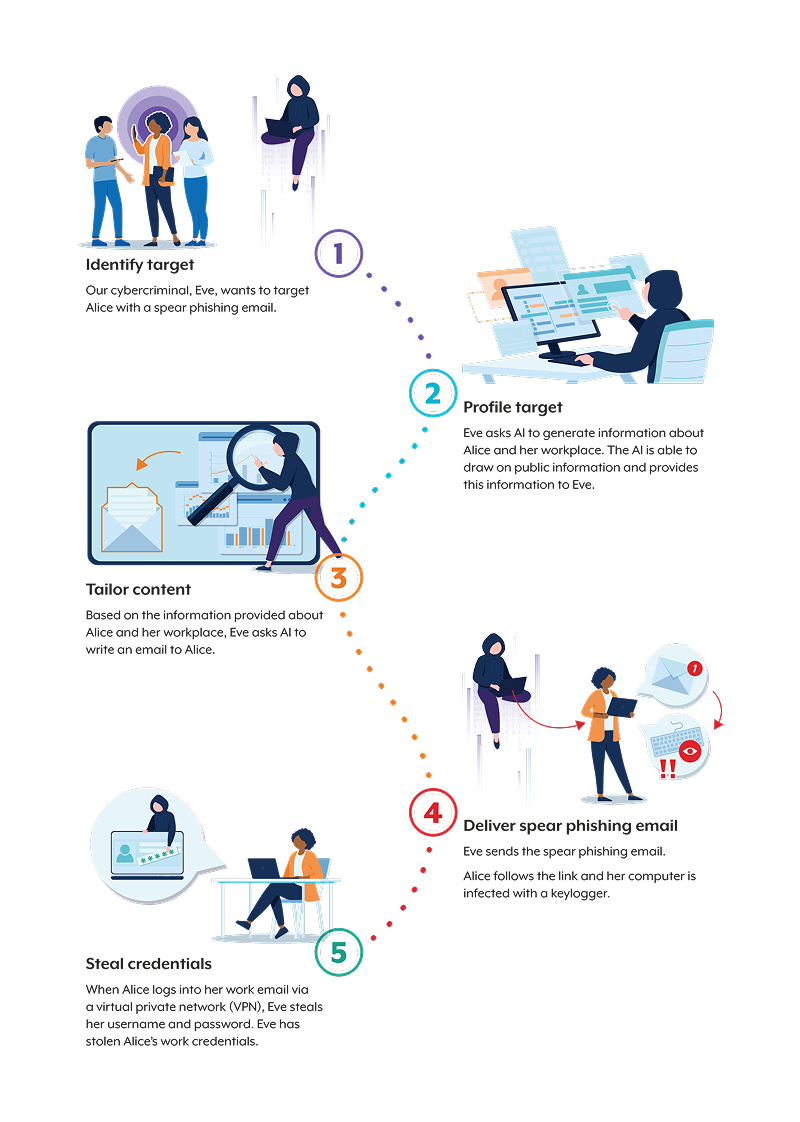
Spear phishing often follows a general 4 key-stage approach:
- Reconnaissance: Attackers choose a target (like your accounts payable officer or new employee) and gather information from public sources. For example, LinkedIn job titles, recent press releases or company social posts.
- Personalisation: With that info, they craft a highly convincing email that looks like part of your normal workflow. Maybe it references a recent project or a known supplier. They might even impersonate a key executive using the same writing style and email signature.
- The Hook: The email asks you to do something—click a link, download an attachment or reply with sensitive info. This often involves urgency (“Need this paid by 5 pm!”) or authority (“As requested by the CFO…”).
- The Catch: Once you bite, attackers might steal credentials, install malware or initiate a fraudulent wire transfer. By the time you realise your mistake, the damage is already done.
Tactics and Techniques
Spear phishers are cunning and resourceful, employing a variety of tactics and techniques to ensure their attacks hit the mark. Here are some of the most common methods they use:
Reconnaissance: Before launching an attack, spear phishers gather as much information as possible about their target. This can include scouring social media profiles, public records, and company websites to build a detailed profile.
Social Engineering: This involves psychological manipulation to trick the target into revealing sensitive information or performing a specific action. For example, an email might appear to come from a trusted colleague, asking for login credentials.
Email Spoofing: Attackers create fake emails that look like they come from a trusted sender. This can involve mimicking the email address, signature, and writing style of the person being impersonated.
Malicious Links and Attachments: Spear phishing emails often contain links or attachments designed to deliver malware or steal sensitive information. These might look like legitimate documents or links to trusted websites.
Urgency and Scarcity: Creating a sense of urgency or scarcity is a common tactic. An email might claim that immediate action is required to avoid a penalty or take advantage of a limited-time offer, pushing the target to act quickly without thinking.
Spear Phishing vs Phishing vs Whaling
Phishing Attack: Think of it as mass spam—broad, general attacks. Scammers send out thousands of emails (like fake PayPal notices) and hope a few people bite.
Spear Phishing: More targeted. The attacker focuses on a specific individual or team and crafts a message just for them.
Whaling: Going after the “big fish”—C-suite execs, high level managers or high net worth individuals. Whaling emails mimic top level communications like a CEO’s request making them even more convincing.
Real World Spear Phishing Examples
Theory is one thing, let’s see what’s been happening in the real world, including right here in Australia.
These broad examples show the growing threat of spear phishing campaigns, targeted attacks personalised for specific individuals and much often much harder to detect.
CEO Fraud
CEO fraud is a type of spear phishing attack where scammers impersonate company executives like your CEO or CFO to authorise suspicious transactions. We’ve seen cases where finance departments receive an email that looks like it’s from the CEO’s account asking for urgent payment of a high value invoice. If the finance manager doesn’t verify it the funds will be transferred straight into criminal hands.
Methods used:
- Impersonating an executive’s email address (sometimes just one letter off)
- Using language and tone of the executive
- Urging immediate action to avoid “business delays”
Outcome: In some cases companies have lost tens of thousands—or more—in a single transfer.
Lessons learned: Always verify unusual requests in person or over the phone. Never rely on an email no matter who sent it.
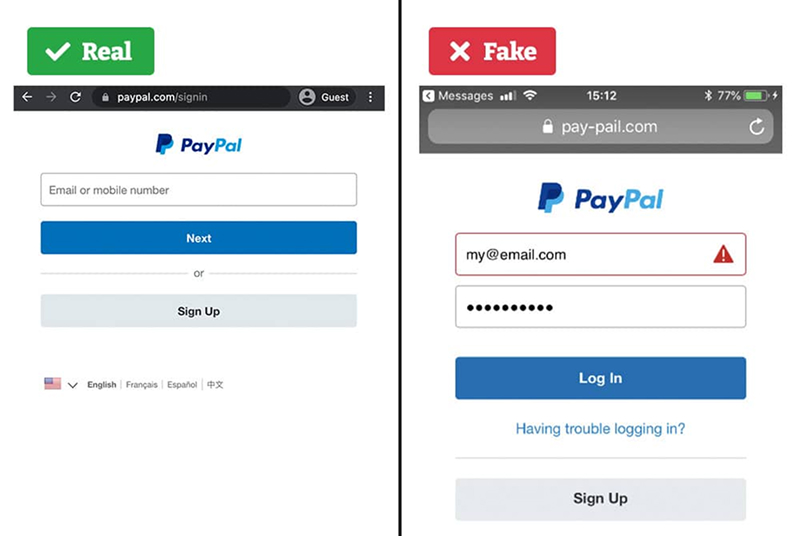
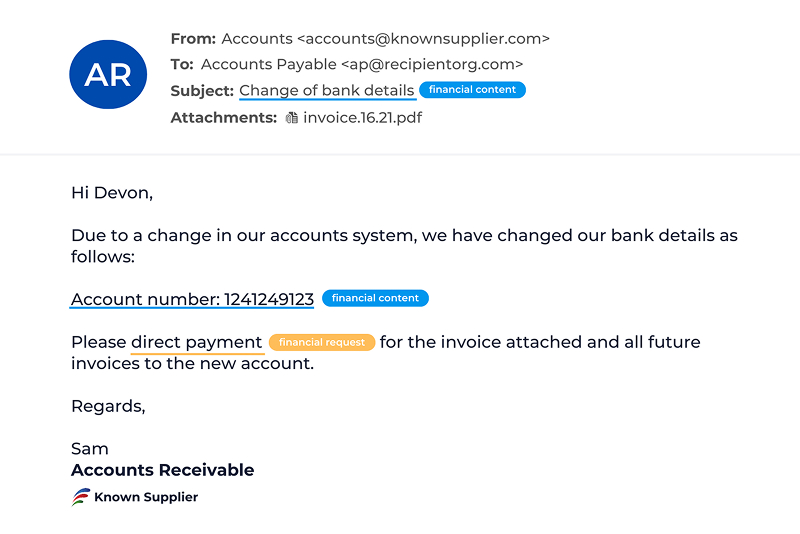
Fake Website and Spear Phishing Emails
Spear phishers may send you a link to a cloned version of a supplier’s website. Everything looks legitimate—the logo, the address, even the contact details but the URL is slightly off. Once you log in the hackers capture your credentials.
Methods used:
- A near perfect copy of a trusted website
- A personalised email asking you to login for “urgent maintenance” or “account verification”
Outcome: Once you login the attackers can use your stolen credentials to place fraudulent orders, access confidential documents or spread more malware.
Lessons learned: Always check URLs carefully. Hover over links before clicking and make sure the site uses valid HTTPS certificates. If unsure, type the company’s known web address directly into your browser.
Malware-Based Attack
Sometimes the attachment in the spear phishing email is the key. Spear phishing attacks often involve a Word doc named “ProjectProposal2024.docx” that looks harmless but opening it triggers a hidden macro that installs malware.
In Australia, an incident involving a Sydney hedge fund Levitas Capital resulted in an $8.7 million scam after an employee clicked on a malicious link disguised as a Zoom invitation.
Methods used:
- Malicious macros in office documents
- Links hidden in PDFs or Excel files
- Messages about ongoing projects or meetings
Outcome: Malware can open backdoors into your network, log keystrokes or allow attackers to pivot further into sensitive data.
Lessons learned: Disable macros by default, scan attachments with antivirus tools and if an attachment looks out of context—verify with the sender before opening.
Business Email Compromise (BEC)
BEC is a term for attacks that hijack or spoof business emails to trick employees. These attacks often involve spear phishing attacks which are targeted and personalised for specific individuals making them much harder to detect. In some Aussie cases attackers have even monitored compromised email accounts for weeks waiting for the perfect moment to insert themselves into a conversation and ask for a payment or sensitive file.
Methods used:
- Gain access to a legitimate corporate email account through stolen credentials
- Monitoring email threads and inserting malicious requests mid-conversation
- Using correct branding, email signatures and referencing ongoing projects
Outcome: Companies may accidentally transfer funds, send valuable IP or expose customer data.
Lessons learned: Implement multi-factor authentication, have strict password policies and train staff to verify requests even if they appear in an ongoing thread.
Phish Out of Water: How to Identify
Spear phishing emails aren’t always easy to spot but here are a few flags to look out for:
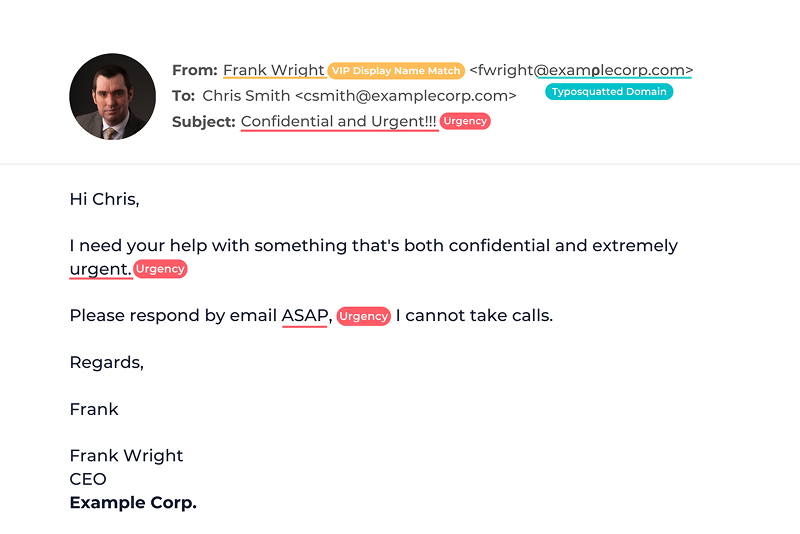
- Suspicious Sender Email: Is the email from an address similar to a known contact but slightly off? e.g. “[email protected]” instead of “[email protected]”
- Unusual Requests: Is someone you trust asking you for something out of the ordinary like a sudden wire transfer or login credentials?
- Urgency and Pressure Tactics: Cybercriminals love to say “ASAP” or “before COB” to rush you into action without thinking.
- Inconsistent Language or Tone: Typos, unusual phrasing or language that doesn’t sound like your colleague’s usual style can be a flag.
- Mis-matched URLs: Hover over links and see if they go where they say they do. If unsure, visit the site via a known bookmarked URL rather than clicking.
Training employees through practical methods like phishing simulations is key to stopping spear phishing.
Prevention Tips to Prevent Spear Phishing Attacks
The good news: there’s a lot you can do to prevent falling victim to spear phishing. Adopting a multi-faceted approach is crucial to effectively prevent spear phishing attacks. It’s all about technology, security awareness training and good old fashioned common sense principles.
Employee Awareness and Security Training: People are your first line of defence. Give them the skills to spot suspicious emails. Consider ongoing education and simulations like phishing awareness training from TechBrain to build a culture of cyber awareness.
Cyber Intelligence: Keep an eye on security alerts from trusted sources (like the ACSC) or look to implement a cyber threat intelligence service. Knowing what’s trending in the threat landscape will help you stay one step ahead.
Network Access Rules and Monitoring: Segment your network and review user access regularly. Limit who can view or edit sensitive data and monitor unusual file transfers or login attempts.
Patch Management: Update software, operating systems and anti-malware tools regularly. Many attacks exploit known vulnerabilities that could have been patched months ago.
Spear Phishing Simulations: Test your team with regular fake spear phishing emails to see who’s paying attention and who needs more training. Learning to spot the signs in a safe environment makes all the difference when the real thing hits.
For more on the human side of manipulation see The Psychology Behind Social Engineering Attacks and for more on defence strategies see Combating Social Engineering Attacks.
Emerging Trends in Spear Phishing
As businesses’ cyber defenses get stronger, criminals adapt. Watch out for these new techniques:
- AI-Driven Attacks: Cybercriminals are using AI to craft even more realistic emails. AI tools can mimic writing styles or respond dynamically to your replies making it harder to spot a fake.
- Deepfake Technology: Video and audio deepfakes could trick you into thinking your CEO called you directly. Imagine receiving a voicemail that sounds just like your boss authorising a payment. It’s not the realm of science fiction, it’s really happening.
- Cloud Service Exploitation: Attackers are targeting cloud platforms like CRMs or accounting software and then pivoting to send emails from these compromised services.
- Cybercrime-as-a-Service: There are entire marketplaces where attackers can buy ready-made spear phishing kits so they don’t need advanced tech skills.
- Mobile-Focused Attacks: As we rely more on our smartphones for business expect more spear phishing via SMS (smishing) or messaging apps to catch you off guard on the go.
Businesses must also be aware of spear phishing threats and use cyber threat intelligence tools and ongoing awareness training to develop their cyber maturity level.
Phishing Season’s Over.
In the vast and ever-shifting landscape of the digital outback, spear phishers are the silent predators lurking beneath the brush.
The difference between falling prey and standing your ground comes down to vigilance, preparation, and smart defences. By sharpening your team’s instincts through dedicated training, double-checking the authenticity of unusual requests, and investing in the right security measures, you transform your organisation from an easy mark into a secure homestead.
At TechBrain, we understand the terrain and are here to help you navigate it with confidence.
Our phishing awareness training and tailored cybersecurity solutions ensure that, even as threats evolve, your business remains steady, unshaken, and prepared for whatever slinks out from the shadows next.
It’s not about never encountering a spear phish—it’s about recognising the tracks, closing the gate and being prepared if a predatory email awaits.