In this article
- What is an Enterprise Password Policy?
- Evolution of Password Policies in Australia
- Essentials of a Modern Password Policy
- Implementation Strategies for Australian Businesses
- Remote Work and BYOD Environments
- Employee Training and Awareness
- The Future of Authentication
- Developing a Comprehensive Password Policy Document
- Building Password Resilience for 2025 and Beyond
Enterprise Password Policy: Australian Best Practices 2025
At TechBrain we have seen a huge increase in cyber-attacks across the Australian cyber landscape, with compromised credentials at the top of the vulnerability list.
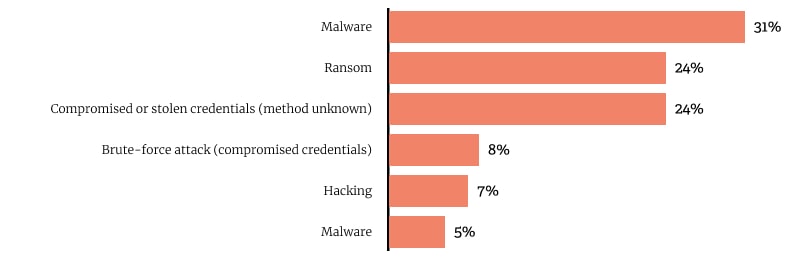
According to the Office of the Australian Information Commissioner’s (OAIC) Notifiable Data Breaches Report: January to June 2024, cyber security incidents involving compromised credentials made up 63% of all breaches during this period and phishing attacks which often lead to compromised credentials was the top cause of breaches. That’s why password policies and user education are crucial to keep data safe and protect your organisation from cyber criminals.
With digital transformation happening fast and remote work the new norm, we recommend Australian businesses upgrade their password management to combat sophisticated and evolving cyber threats. Tell your customers and vendors to up their online security when they do business with your organisation.
Passwords are the first line of defence but they are also one of the weakest links in an organisation’s security posture. The complexity and changing nature of cyber threats mean Australian businesses must not only have a password policy but continually refine it to stay protected.
This guide will show you how to create user friendly password policies aligned to current best practice and Australian compliance requirements.
What is an Enterprise Password Policy?
An enterprise password policy is a formalised set of guidelines outlining best practices for password creation, use, management, security and retirement within an organisation. Effective policies include robust criteria for password complexity, length, rotation, storage, multi-factor authentication (MFA), recovery mechanisms and ongoing user education.
These policies tell users to choose a secure password and prompt them to choose a different password if their initial choice is weak or compromised.
An enterprise level password manager can simplify password management for employees by creating, storing and auto filling strong passwords. Well designed policies not only reinforce organisational security but also align to compliance frameworks like the Australian Cyber Security Centre’s (ACSC) Essential Eight and international standards such as ISO 27001. These policies ensure regulatory compliance, operational resilience and reduce credential related cyber security risks.
For Australian businesses in regulated industries, password policies also help demonstrate compliance with sector specific requirements such as APRA’s CPS 234 Information Security standard for financial services or the Security of Critical Infrastructure Act 2018 for essential services providers.
Evolution of Password Policies in Australia
Historically, Australian organisations focused on frequent password rotation, strict complexity rules and short passwords. But current ACSC guidance is for longer, memorable passphrases that are hard to hack and robust MFA. This is a big shift towards usability and security.
This brings Australian practices more in line with international benchmarks like NIST SP 800-63B which advocates for simplicity, longer passwords and minimising password rotation. Recognising the human factor in password management has been a big step forward for security and user compliance. And don’t use personal information like names in password creation to prevent social engineering vulnerabilities.
The shift recognises a fundamental truth: security measures that create too much friction will have users develop workarounds that reduce security. Today’s best practice balances security with usability, acknowledging human behaviour as a critical component of password management.
Essentials of a Modern Password Policy
Password Length and Complex Passwords
ACSC now recommends passwords of at least 14 characters, and organisations should encourage them to adopt passphrases. Easy to remember sentences that increase complexity through length not difficult to remember character combinations.
A long complex password is more secure against brute force attacks. This increases password entropy and user adoption rates across all organisations. Including symbols in passwords makes them much harder for hackers to crack during brute force attacks.
For Australian organisations updating their password policies, practical guidelines include:
- Minimum length of 14+
- Allowing spaces and all printable characters
- Focusing user education on constructing memorable passphrases
- Avoiding arbitrary composition rules that frustrate users
Organisations should educate employees regularly on building secure passphrases that are easy to remember but hard for attackers to guess, using examples and interactive training sessions.
Password Expiration, Rotation and Password Resets
Mandatory password rotation was always the default but is now widely recognised as counterproductive in cyber security best practice, especially with password change policies.
Frequent forced changes have led users to choose predictable or incrementally modified passwords. The ACSC now recommends password changes only when compromise is suspected or confirmed. And require employees to use strong passwords to protect against hacking. Clearly communicate this transition to users to ensure a smooth transition and higher compliance across the organisation.
The current ACSC recommendation is that passwords should only be changed when:
- There is evidence or suspicion of compromise
- If you want to change the password for other reasons (e.g. privacy concerns)
- The user requests a change
- A specified period of extreme length (e.g., once per year) has passed as a backstop measure.
Supplement with real-time breach monitoring and targeted password resets if a breach is detected.
Multi-Factor Authentication
Multi-factor authentication is now a required practice for Australian organisations. The Essential Eight requires MFA for sensitive and privileged user accounts. Organisations must assess their security needs and operational capacity when choosing MFA methods including authenticator apps, hardware tokens, biometrics or SMS verification which require multiple forms of authentication.
Australian businesses should consider:
- MFA for remote access, privileged accounts and cloud services
- MFA for different systems based on risk profile
- Contingency plans for lost or unavailable MFA devices
- Clear user guidance and support during implementation
Stronger passwords and authentication makes it harder for attackers to get to your data.
Regular training sessions should cover the importance of MFA to ensure wide adoption and build understanding of its role in your organisation’s security.
Password Screening and Blocklists
Automated password screening tools and comprehensive blocklists of compromised passwords reduces credential vulnerability.
Update your blocklists regularly to prevent weak or common passwords from being created and you’ll minimise the risk of credential stuffing and brute force attacks. Implement a retry mechanism to manage failed login attempts like temporary account lockouts and time doubling between each retry to enhance security and protect your data.
A good password screening system should check proposed passwords against:
- Common passwords (e.g. “password123”, “qwerty”)
- Contextual information (company name, username etc.)
- Passwords exposed in known data breaches
- Simple keyboard patterns (e.g. “asdfgh”)
Regularly review and update your blocklists to stay ahead of evolving threats and commonly used insecure passwords.
Secure Password Storage and Transmission
Strong password security requires advanced hashing algorithms with unique salts to prevent unauthorised access. Never store password data in plain text or reversible encryption. All password exchange should be over secure encrypted channels that comply with Australian Privacy Principle (APP) 11.
For system administrators and security professionals consider:
- All password entry points use TLS encryption
- Appropriate password hashing with sufficient computational complexity
- Monitor for credential exploitation
- Separate storage for authentication systems from application data
Semi-regular security audit and penetration testing practices to verify these standards is recommended to ensure all storage and transmission is up to best practice standards.
Implementation Strategies for Australian Businesses
For Smaller Businesses
- Use built-in security features in modern identity providers (Microsoft 365, Google Workspace)
- Implement a company wide password manager to require employees to use strong unique passwords
- Focus on employee education and awareness rather than complex technical controls
- Prioritise MFA for all users especially email and financial systems
- Consider cloud based security services that includes password policy management, work with IT staff or service provider to require employees to follow the policies
For Enterprise Organisations
- Centralise identity management with granular password policy controls
- Tier policies based on risk and account privilege levels
- Ask staff to change all default credentials on software and hardware products to mitigate security risks
- Use advanced authentication solutions, potentially biometrics and conditional access
- Password managers can assist to remember complex passwords and ensure strong password practice
- Continuous compliance monitoring and reporting
- Passwordless authentication where applicable
Remote Work and BYOD Environments
The shift to remote and hybrid work in Australia has created new password security challenges. When employees access corporate systems from home networks and personal devices, traditional perimeter based security controls become less effective.
Users must be guided to select secure passwords and prompted to choose another one if the initial choice doesn’t meet organisational security criteria.
The key considerations for password security in distributed workforces are:
Enhanced MFA for remote access:
- MFA for all remote connections
- Conditional access based on device health and network
- Geo-fencing for high-risk services
Device management for password security:
- Device encryption
- Screen timeouts and lock policies
- Mobile device management (MDM) solutions
Network level protections:
- VPN for sensitive systems
- DNS filtering for phishing sites
- Zero Trust Network Access (ZTNA) approaches
Password manager deployment:
- Enterprise password management for remote teams
- Secure sharing of team passwords
- Browser integration to prevent manual password entry
Implement these security measures to protect user identity, organisational data and comply with security standards.
Security vs productivity remains key. Too much friction in authentication can lead remote workers to create workarounds that reduce security not increase it.
High Risk Industries and Functions
Certain industries in Australia are at higher cyber security risk due to the sensitivity of their data or critical infrastructure. Financial services, healthcare, government and essential services providers should implement additional password security measures and require employees to use strong passwords.
Enhanced requirements for privileged accounts:
- Longer password length (20+ characters)
- Hardware security keys for authentication
- Just-in-time access provisioning
- Session recording and monitoring
Industry specific compliance requirements:
- APRA CPS 234 for financial services
- My Health Records Act for healthcare providers
- Security of Critical Infrastructure Act requirements
- Australian Government Information Security Manual (ISM)
Risk based approach to password policies:
- Tiered authentication based on data sensitivity
- Enhanced monitoring for critical systems
- Break-glass procedures for emergency access
Organisations in healthcare should review our recent healthcare cyber security article for sector specific guidance on protecting patient data while maintaining clinical workflow efficiency.
Employee Training and Awareness
Training Employees for Password Security Success
Employee training and awareness is key to password policy success. Employees must understand the importance of password security and how to create and manage strong passwords. Training employees on password security best practices can prevent cyber threats and protect personal and business accounts.
Organisations should provide regular cyber awareness training sessions to educate employees on password security best practices such as:
- Creating complex and unique passwords
- Avoiding password reuse and phishing attacks
- Using password managers and multi-factor authentication
- Understanding the importance of password security and the consequences of weak passwords
By training employees on password security best practices, organisations can create a culture of vigilance and encourage employees to be the first line of defence against cyber threats. Regular training ensures employees stay up to date with latest security practices and understand their role in securing personal and business accounts.
Educating Users on Password Reuse and Phishing Avoidance
Organisations should educate users on the risks of password reuse and phishing attacks and provide guidelines on how to avoid them.
- Avoiding the use of the same password for multiple accounts
- Being cautious when clicking on links or downloading attachments from unknown sources
- Verifying the authenticity of emails and websites before entering sensitive information
- Using password managers and multi-factor authentication to protect accounts
By educating users on password reuse and phishing avoidance organisations can stop cyber threats and protect personal and business accounts. Clear guidance and practical advice empowers employees to take proactive steps to secure their credentials and the overall cyber security posture of the organisation.
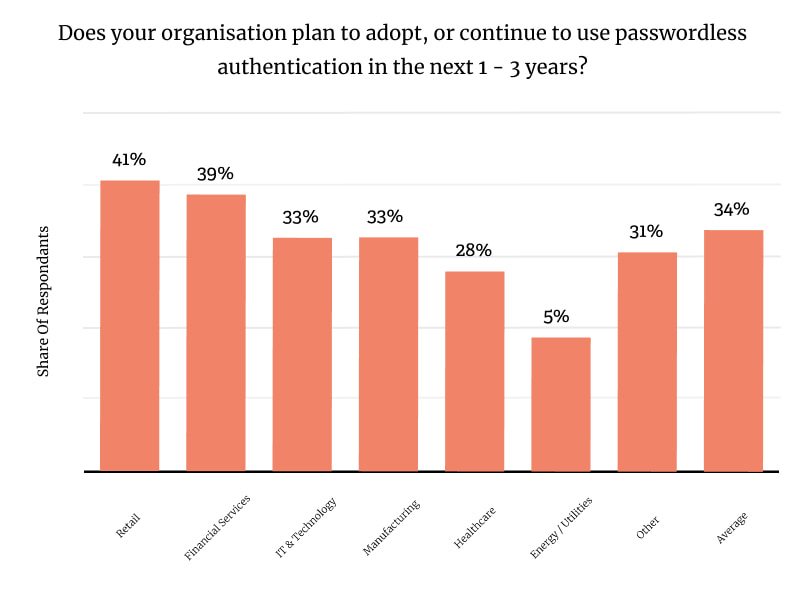
The Future of Authentication
Passwordless Options
The cyber security industry is moving to passwordless solutions like biometrics, hardware security keys and Single Sign-On (SSO). These solutions are more secure, eliminate password risks and simplify user authentication.
But organisations need to address the issues of interoperability, user acceptance, device compatibility and operational integration.
Emerging Standards and Technologies
New authentication standards like FIDO2 and WebAuthn, combined with adaptive authentication and AI driven behavioural analytics are becoming mainstream in Australia making it harder for attackers to get to sensitive data.
Organisations should follow these emerging solutions and integrate them into their cyber security frameworks to stay secure and future proof.
Developing a Comprehensive Password Policy Document
A well-crafted password policy document is essential for clear communication and consistent implementation, making it harder for attackers to gain access to sensitive data. Essential elements need to include:
Purpose and scope:
- Statement of purpose
- Systems and users covered by the policy
- Relationship to other security policies
Password requirements:
- Length and complexity guidelines
- Account lockout thresholds
- Special requirements for privileged accounts
Password lifecycle management:
- Creation, reset and expiration procedures
- Conditions for password change
- Handling of suspected compromise
Multi-factor authentication requirements:
- When MFA is required
- Approved authentication methods
- Exceptions and contingency procedures
Enforcement and compliance:
- Technical controls and monitoring
- Consequences of non-compliance
- Audit procedure
In the interest of a simple, user-friendly document. Use clear language, provide examples of acceptable passphrases and explain the reasoning behind the requirements rather than just listing the rules.
Need a more comprehensive IT security policy beyond password guidance? Check out our ICT policy guidelines.
Building Password Resilience for 2025 and Beyond
Password policies have evolved from arbitrary complexity to length, uniqueness and additional verification factors making it harder for attackers to get in. We urge Australian organisations to adopt these modern approaches to improve security, user experience, and ultimately, safeguard business continuity.
Key recommendations for Australian businesses in 2025:
- 14+ character password length
- Remove arbitrary complexity and mandatory rotation
- MFA for all users
- Screen passwords against breach databases and common passwords
- Use password managers to create strong unique passwords
- Go passwordless where you can
By implementing the recommendations in this guide you will not only reduce password breaches in your organisation, but also make life easier for your users. Remember that password security is not only a critical part of a robust cyber security strategy; it’s the foundation on which cyber maturity is built.
Need help with your password policies and authentication? Get in touch with our cyber security experts today to discuss how we can help your organisation get cyber secure, and up to 2025 best practice.