In this article
Let’s be real, keeping Australian financial institutions secure these days is a never ending battle. Cyber threats, from ransomware locking down systems to sneaky data breaches are relentless, diverse and the fallout can be huge – to your bottom line, operations and customer trust.
As guardians of sensitive data and the critical infrastructure that keeps our economy running, financial institutions like yours are a prime target. Recognising this high stakes environment, the Australian Prudential Regulation Authority (APRA) introduced Prudential Standard CPS 234.
Don’t think of this as just another compliance box to tick. Think of it as a framework to help you strengthen your cyber resilience and protect what matters most. Remember these safeguards aren’t just for your internal teams; they extend to any third party that handles your information assets.
So whether you’re the IT manager in the trenches figuring out how to implement security controls or the business leader steering the ship and accountable for overall risk and governance, getting to grips with CPS 234 is essential.
Think of this guide as your practical blueprint.
We’ll break down what CPS 234 means for you, your obligations, the key requirements without the jargon, common pitfalls (and how to get around them), its relationship with CPG 234 and other frameworks like ISO 27001 and show you how building a sustainable compliance program can be a real asset to your business.
What is APRA CPS 234?
APRA CPS 234 is a prudential standard that requires regulated entities to have robust information security. In short, it’s about being prepared and resilient to information security incidents, especially cyber attacks.
To achieve this, you need to have an information security capability.
This means having the right mix of policies, security controls, skilled people and processes in place. The strength of this capability needs to be proportionate – i.e. suitable for the specific vulnerabilities and threats your organisation faces, given the size and complexity of your operations.
Crucially, the scope of CPS 234 is wide. It applies to all your information assets (like sensitive data and the systems that manage it), whether managed by your internal teams or external third-party service providers.
You need to have controls in place to protect these assets from unauthorised access or disruption so you can safeguard the information that’s critical to your organisation and your customers.
Who Needs to Comply and Compliance Obligations
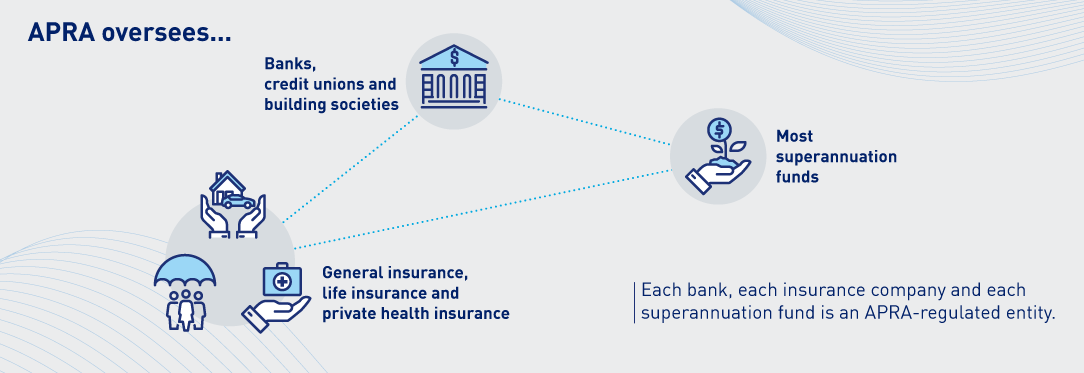
Compliance with CPS 234 is mandatory for all APRA regulated entities.
- Banks (Authorised Deposit-taking Institutions or ADIs)
- General Insurers and Reinsurers
- Life Insurance companies
- Private Health Insurers
- Superannuation Trustees (RSE Licensees)
Boards have a key role to play in managing information security risks, particularly under APRA CPS 234. They need to understand their obligations and establish clear information security policies to be resilient to cyber threats.
But the responsibility doesn’t stop at the entity’s own perimeter. CPS 234 explicitly requires entities to manage information security risk associated with the use of third party service providers (including parent companies, offshore providers and cloud services) that manage information assets on their behalf. If a third party handles your sensitive data or critical systems you are responsible for ensuring their security meets the standard.
The consequences of non-compliance can be severe – from increased regulatory scrutiny and formal warnings to significant fines, enforceable undertakings and even director disqualification. Beyond regulatory penalties failing to meet CPS 234 standards increases the risk of security incidents, financial loss, operational disruption and erosion of customer trust.
But businesses would be naive to look at CPS 234 through the lens of avoiding regulatory punishment, compliance delivers real business benefits – enhanced cyber resilience, stakeholder confidence, stronger risk management practices and potentially a competitive advantage.
APRA CPS 234 Key Requirements
APRA CPS 234 outlines a framework with several key pillars to strengthen the information security of regulated entities by specifying the information security requirements of the standard.
Understanding these interrelated requirements is crucial for implementation and oversight across the organisation.
Information Security Capability
CPS 234 requires an information security capability—technology, people, processes and resources that is proportionate to the entity’s size, complexity and specific cyber threats.
This means clearly defined security roles and responsibilities across the board, management and committees. Entities must also assess third party provider capabilities, IT resources are fit-for-purpose and business leaders are championing the necessary investment.
Policy Framework
A board approved information security policy framework is the core governance instrument, defining the approach to managing security risks across roles, asset classification, access controls, incident response and third party risk.
This framework requires regular review (at least annually) and timely updates to reflect changing threats and business needs, to ensure the business risk appetite overseen by leaders and the technical standards implemented by IT managers are aligned.
Information Assets
From the policy entities must systematically identify and classify critical information assets (data, hardware, software) by business criticality and confidentiality to determine the required security controls.
This includes assets managed by related or third parties. Understanding asset dependencies is key to risk assessment and business continuity requires IT (for inventory) and business units (for impact context) collaboration.
Controls
With assets identified and classified the focus then turns to controls.
CPS 234 requires a risk based approach, so control selection must be proportionate to the asset value and the specific threats. It’s important to understand and review the design of information security controls to ensure they protect the information assets and meet the standard.
These controls are not static; they must protect the information assets throughout their entire lifecycle from creation or acquisition to secure destruction. While the mix of controls will vary depending on the risks, key categories will always include:
- Access control: Strong password policy principles like least privilege, multi-factor authentication and regular access reviews.
- Network security: Firewalls, intrusion detection and prevention systems and network segmentation.
- Data protection: Encryption for data at rest and in transit, data loss prevention and secure data handling practices.
- System security: Change management processes, timely patching of vulnerabilities and secure configuration standards.
- Physical security: Physical access to sensitive hardware and data centers. The implementation and ongoing monitoring of these technical controls is the responsibility of IT, guided by the risk tolerance and strategic oversight from Business Leaders.
Incident Management
Entities need to have mature incident management capabilities, integrating business continuity into documented plans and resources to detect, respond to and recover from security incidents.
These plans must detail detection methods, response procedures, roles, escalation paths and communication strategies. Regular testing through practical simulations or tabletop exercises is essential to validate their effectiveness and organisational resilience.
Testing Control Effectiveness
In addition to incident preparedness, CPS 234 requires a program to periodically test the operational effectiveness of key controls.
The nature, frequency and depth of testing (using common methods like vulnerability assessments, penetration tests and configuration audits) must align with asset criticality and the evolving threat landscape. APRA stresses independent testing to provide objective assessment and credible assurance to the Board and senior management regarding the security posture.
Internal Audit
In addition to this assurance function the entity’s internal audit team (or equivalent independent function) must play a key role. Internal audit must review and assess the overall adequacy and effectiveness of the entity’s information security controls to ensure they are in place.
This includes reviewing controls related to third party arrangements. The scope and frequency of these audits must be sufficient to provide a reliable independent view of the control environment. Documenting findings and tracking management’s remediation actions is key to this process.
APRA Notification
Transparency with the regulator during significant security events or upon discovery of major weaknesses is critical. CPS 234 requires specific notifications to APRA under defined circumstances:
- Within 72 hours: Entities must notify APRA when they become aware of a significant information security incident that will impact the entity or its customers.
- Within 10 business days: Notification is required when a material security control weakness is identified that can’t be remediated quickly.
APRA operates independently to provide assurance under all reasonable circumstances, particularly around stability and security in the financial sector. These timeframes show how important APRA is on timely awareness and management of critical information security issues.
CPS 234 vs CPG 234: What’s the Difference?
While often mentioned together, CPS 234 and CPG 234 serve different purposes:
- APRA CPS 234 (Prudential Standard): This is the mandatory minimum requirements that all APRA-regulated entities must comply with. It outlines what needs to be achieved for information security. It is legally binding.
- APRA CPG 234 (Prudential Practice Guide): This is guidance, not mandatory regulation. It provides examples, methodologies and better practice guidance on how entities can meet the requirements in CPS 234. It clarifies APRA’s expectations.
Think of CPS 234 as the law and CPG 234 as the instruction manual. While not binding, aligning with CPG 234 shows a mature approach to compliance and helps interpret the often principle-based requirements of the standard. Both should be used together to develop information security capability.
Common Challenges & Practical Solutions
Achieving and maintaining CPS 234 compliance has several common hurdles.
Entities must align their testing programs with the frequency of change in cyber threats and vulnerabilities to ensure effective control testing within GRC software.
Asset Identification and Classification
Many entities struggle to maintain a complete, accurate and classified inventory of their information assets, especially in complex, dynamic environments.
The number of security vendors in the Australian market adds to this complexity, so understanding the number of entities regulated by the regulator for compliance and risk management is key.
Solution: Use automated discovery tools where possible. Define clear ownership and review cycles involving IT and business units. Create a practical classification schema based on business impact, not technical attributes. Start with critical assets and expand.
Third-Party Risk
Managing the security of many third-party arrangements (especially cloud providers or offshore services) is complex and resource intensive. Getting transparency is hard.
You must continuously monitor third-party vendors’ security controls and risk levels to ensure compliance and manage cyber risks.
Solution: Develop a tiered risk assessment process for vendors. Embed security requirements and audit rights into contracts. Leverage independent certifications (like SOC 2, ISO 27001) where available but supplement with questionnaires and evidence reviews for high-risk providers. Review vendor performance against contractual obligations regularly.
Incident Response
Developing practical, tested incident management plans that go beyond theory and work under pressure is hard work. Coordinating different teams during a crisis is often harder than expected.
Scanning is one of the detection mechanisms required by CPS 234. This involves using scanning alongside other solutions like monitoring and logging to detect and respond to information security incidents in a timely manner.
Solution: Run regular, realistic scenario-based testing (tabletop exercises, simulations). Define roles, responsibilities and escalation paths before an incident. Invest in detection technologies (like SIEM/SOAR) and make response playbooks practical and accessible.
Roles and Responsibilities
Getting clarity and accountability for information security across the organisation, especially beyond formal sign-off with the Board.
Individuals within organisations must know their responsibilities during incidents to ensure information security roles are clearly defined across different levels of governance.
Solution: Document roles and responsibilities within the information security policy framework. Provide tailored training and awareness programs for different groups (Board, management, staff).
Report to the board regularly on risk posture, key metrics, incident trends and assurance results.
Compliance and Control Effectiveness
Moving beyond having controls to consistently proving their effectiveness through testing and audit requires structured processes and resources.
Ultimately, the board is responsible for ensuring compliance with CPS 234, so they have the final say in information security and standards.
Solution: Develop a formal assurance plan outlining testing schedules, methodologies and scope. Use a mix of internal and external testing. Automate control checks where possible. Document test results and remediation tracking for audit purposes.
CPS 234 vs ISO 27001
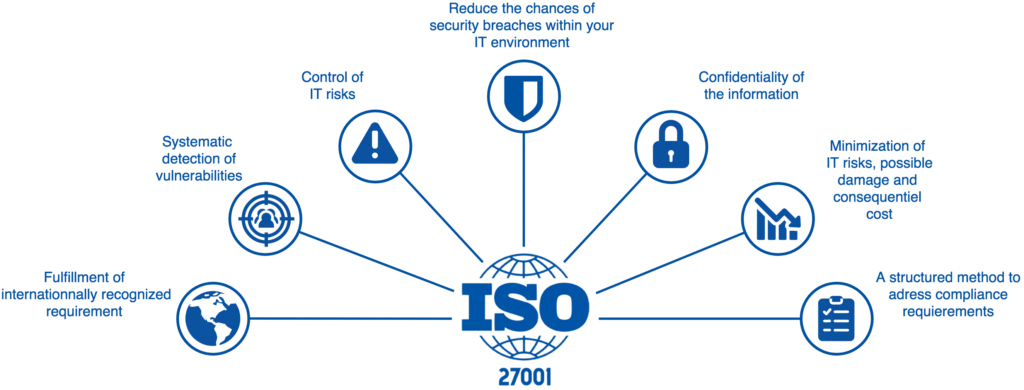
There is a lot of overlap and synergy between APRA CPS 234 and the international standard ISO 27001 for Information Security Management Systems (ISMS).
APRA regulated entities need to have information security systems and practices to combat cyber threats. CPS 234 is the framework for entities to enhance their security, mitigate risks and comply with regulations around sensitive data.
Similarities
Many of the core requirements of CPS 234 (e.g. policy framework, risk assessment, asset management, access control, incident management, control testing, internal audit) are part of an ISO 27001 ISMS.
Benefits for ISO 27001 Certified
Entities already certified to ISO 27001 have a strong foundation to meet CPS 234 requirements. The existing ISMS provides the structure, processes and evidence to demonstrate compliance. It’s much easier.
Strategic Approach
Even if not certified, using the ISO 27001 framework provides a risk-based approach to implementing and managing information security controls that aligns with APRA’s expectations. It provides a unified approach, mapping CPS 234 requirements to ISO 27001 controls.
Using ISO 27001 simplifies CPS 234 compliance, governance and provides internationally recognised assurance of your security posture.
Business Benefits Beyond Compliance
CPS 234 is more than just compliance. Embedding its principles delivers real business value:
- Security Posture: Toughens up your defences against costly breaches and operational disruption, improves overall cyber resilience.
- Governance: Clarifies accountability, improves risk management discipline and visibility of security risks to the Board and senior management.
- Competitive Advantage: Being able to demonstrate robust data security and regulatory compliance is a customer differentiator.
- Cyber Maturity: CPS 234 is the baseline. Implementing it gets you to the next level of cyber security maturity and prepares you for future threats and regulatory expectations.
Financial institutions use third party tools and services to improve customer experience. While this improves service delivery it also increases risk for those entities.
Key Tools and Guides for CPS 234
CPS 234 requires a structured approach, often supported by specific tools and methodologies. Clearly defined information security functions are critical for CPS 234 compliance, ensuring responsibilities are well defined to avoid fragmentation and lack of ownership. Consider these essential elements:
Cyber Risk Assessment
CPS 234 starts with understanding your unique risks. A formal cyber risk assessment helps identify critical information assets, analyse relevant threats and vulnerabilities, evaluate existing controls and prioritise remediation activities.
Cyber attackers are always evolving their tactics, so APRA regulated entities must follow the CPS 234 framework to stay ahead.
ISO 27001 Framework / ISMS
As mentioned, using the ISO 27000 family of standards provides a solid framework for your Information Security Management System (ISMS) to structure policies, controls, risk management and continuous improvement for CPS 234.
The Australian Prudential Regulation Authority (APRA) regulates various financial institutions, including credit societies, as part of its mandate to ensure financial stability and consumer confidence in the community.
Cyber Maturity Models
Assessing your current information security capability against a recognised maturity model helps identify strengths and weaknesses across different domains (people, process, technology) and provides a roadmap for improvement aligned with CPS 234 and broader best practices.
Systems and networks must be protected from the increasing frequency and sophistication of cyber-attacks, especially for financial institutions handling sensitive information.
Ongoing Compliance
CPS 234 compliance isn’t a one-off project; it’s an ongoing commitment.
- Integration: Embed information security into broader risk management frameworks, business processes and technology lifecycle management.
- Continuous Improvement: Regularly review and update policies, controls and response plans based on testing results, audit findings, threat intelligence and evolving business needs.
- Adaptation: Stay informed about regulatory changes, emerging threats and new technologies to ensure your security posture remains effective.
- Culture: Foster a security aware culture through ongoing training and clear communication of roles and responsibilities.
- Automation: Leverage technology where possible to automate control monitoring, testing and reporting for efficiency and consistency.
Ask specific questions to address compliance obligations and evaluate security capabilities. This proactive approach helps understand regulatory requirements and manage third-party risks.
By treating information security as a continuous cycle of assessment, protection, detection, response and improvement, organisations can build a truly sustainable and resilient compliance program.
The Information Security Journey Doesn’t End, It Evolves
Think of meeting APRA CPS 234 as laying the foundation, not crossing the finish line.
For you, IT managers or business leaders, getting this right goes way beyond just ticking the regulator’s box. It’s about protecting your daily operations, your reputation and the trust your customers have in you.
By using the guidance in CPS 234, learning from common mistakes and maybe using frameworks like ISO 27000, you’re building real cyber resilience. But remember, threats change, technology evolves and your business grows. Being secure means treating this as an ongoing commitment, constantly adapting and strengthening your approach.
Feeling like you need a partner on this journey? If you need help with CPS 234 complexities or taking the next step in your security maturity, the team at TechBrain are here to help. Get in touch today to chat about our cyber risk assessments, ISO implementation support and custom ICT security policy services.