In this article
Welcome to the world of cyber forensics, where technology meets investigation. As more of our work and personal lives move online, getting to the bottom of digital incidents has become essential. Cyber forensics is no longer something that sits in the background of police dramas. It helps people recover from scams, supports internal investigations, and gives businesses the facts they need after an incident.
Think about your day. Payments, messages, file sharing and logins all leave a trail. If something goes wrong, that trail is what tells the story. Cyber forensics is the discipline that follows those clues, explains what happened, and helps prevent a repeat. It is equal parts technology, process and clear thinking.
What Exactly Is Cyber Forensics?
Definition: Cyber and digital forensics is the structured collection, preservation and analysis of digital evidence so it can be relied on in investigations and in court. It requires care, repeatable methods and an understanding of both the technology in play and the legal standards that apply.
Types of Cyber Forensics
Different specialisations focus on different sources of truth. Knowing which one to lean on speeds up investigations and improves outcomes.
Database Forensics
Deep analysis of databases and their metadata. Practitioners review logs, transaction histories and in-memory states to track unauthorised use, spot tampering and recover deleted entries. It is common in fraud, intellectual property and insider threat matters.
Email Forensics
Recovery and analysis of emails and their headers, routes and attachments. This work helps trace phishing campaigns, confirm who sent what and when, and reconstruct the sequence of events around an incident.
Malware Forensics
Disassembling and studying malicious code to understand how it arrived, what it does and how far it spread. Findings feed into detection rules, containment steps and long-term hardening.
Memory Forensics
Analysis of volatile data in RAM. It can reveal running processes, decrypted content, credentials in use and attacker tooling that never touched the disk. It is particularly useful in live incident response.
Mobile Forensics
Extraction and review of data from phones and tablets, including messages, app data and location artefacts. This can place activities on a timeline and connect people, devices and places.
Network Forensics
Inspection of network traffic and logs. Packet captures, flow data and proxy records help identify initial access, command and control, data exfiltration and lateral movement.
These areas often overlap in a single case. A strong outcome usually blends multiple sources of evidence to build a clear timeline and a confident conclusion. For businesses, understanding the options helps shape better response plans and smarter prevention.
The Cyber Forensic Process Unveiled
The work follows a repeatable path. Each stage matters. Skipping steps risks losing evidence or drawing the wrong conclusion.
Identification
Spotting red flags
Teams look for indicators of compromise, such as unusual traffic patterns, suspicious authentication attempts or files that change without explanation.
Initial assessment
The aim is to understand what is affected, how severe it looks and what to do first.
Preservation of scene
Protect what is there. Isolate systems if needed, pause automated clean-ups, and secure logs so data is not overwritten.
Collection
Gathering evidence
Create forensic images of disks, capture memory where appropriate, collect log data and export relevant cloud artefacts. The rule is to work from copies, not the original.
Maintaining integrity
Use write blockers, record the chain of custody and document every action. This keeps evidence admissible and the analysis repeatable.
Analysis
Using the right tools
Review file systems, logs, memory and network data. Recover deleted items, decode artefacts and correlate events across sources.
Reconstructing events
Build a timeline that explains what happened, when and by whom. Link actions to known techniques and tools.
Attribution and methods
Where possible, identify the approach taken by the attacker and the controls that failed or were missing.
Reporting
Documenting findings
Present the scope, the methodology, the evidence and the conclusions. Keep the narrative tight and the references precise.
Clear presentation
Summaries, timelines and simple visuals help non-technical readers follow the logic.
Recommendations and next steps
Outline containment, eradication and recovery, then list changes to reduce the chance and impact of a repeat event.
This process blends technical depth with discipline. Done well, it answers three questions every executive asks after an incident: what happened, how bad is it, and what are we doing about it.
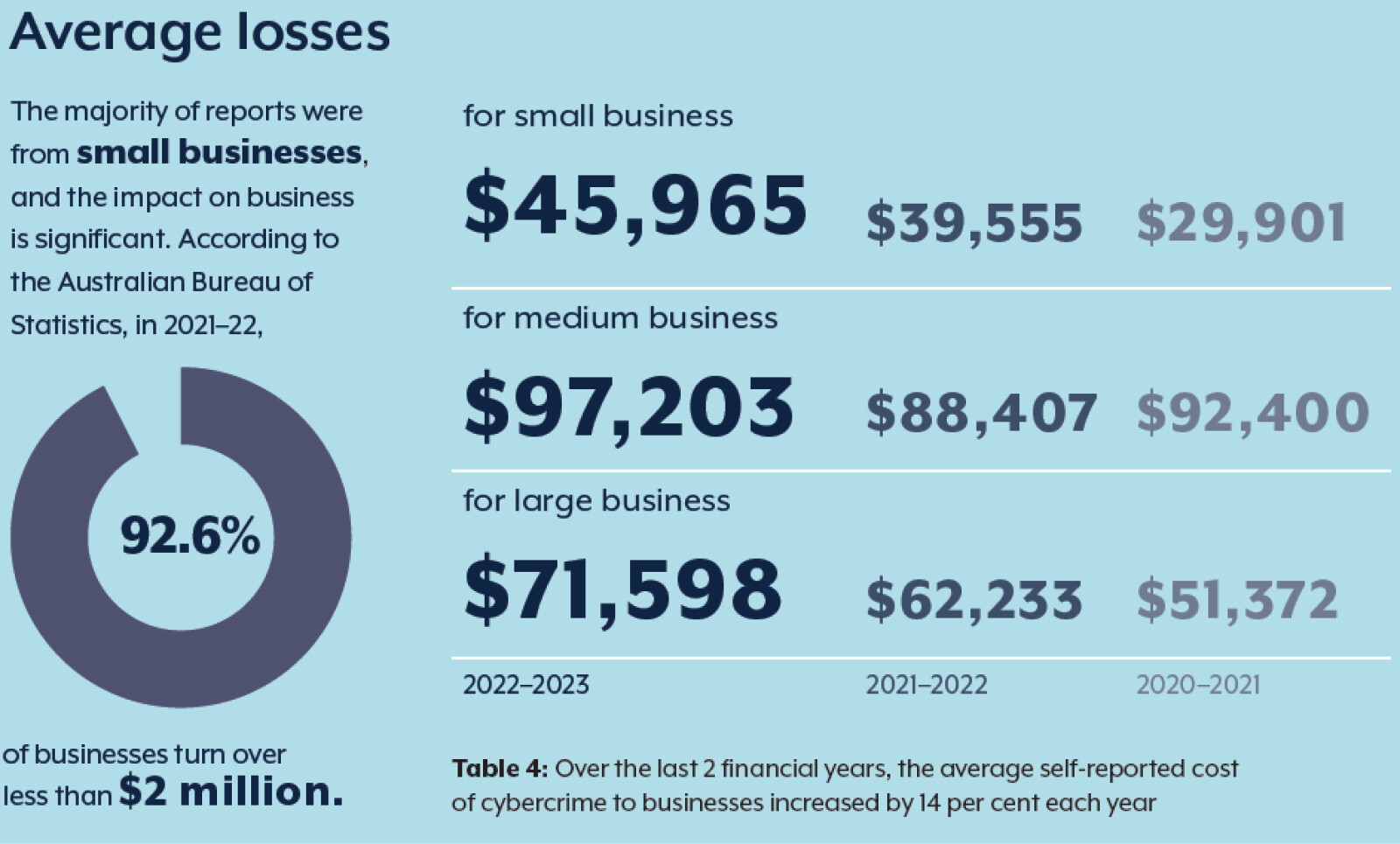
The Rising Importance of Cyber Forensics
The cost of a breach is not just a bill for cleanup. It can disrupt operations, damage trust and invite regulatory scrutiny. High-profile cases such as the Equifax breach have shown how quickly a data leak can spiral. Forensics is central to understanding exposure, meeting notification duties and backing your public statements with facts.
Compliance expectations have grown too. Privacy and data protection regimes in Australia and overseas require prompt, accurate reporting. Forensic records and artefacts support that process. They also help when insurers ask detailed questions about cause, scope and controls.
Enabling a Proactive Approach to Cyber Security
Forensics is not only a post-incident activity. The same skills and tools can harden your environment.
Identifying potential vulnerabilities
Routine reviews of network architecture, identity controls and logging uncover weak points before an attacker does. Testing backups and recovery paths proves you can restore quickly.
Assessing risk exposure
Risk is not purely technical. Process gaps and human error create openings. Forensic thinking looks at how people work, what systems record, and whether there is enough detail to reconstruct events if needed.
Developing robust strategies
Evidence from past incidents feeds directly into your roadmap. Priorities often include better identity hygiene, stronger monitoring and response, tighter admin practices and training that reflects real attack patterns. The goal is to make detection faster, containment cleaner and recovery predictable.
Pursuing a Career in Cyber Forensics
It is a field for people who like puzzles, patterns and practical outcomes. The work ranges from hands-on analysis to advising boards.
Forensic Computer Analyst
Focuses on imaging, examination and recovery across devices and platforms. Turns raw artefacts into facts that hold up under scrutiny.
Cyber Security Analyst
Monitors and defends systems. Partners with forensic teams during and after incidents, then folds lessons into controls and automation.
Incident Responder
Works under time pressure to contain threats, collect volatile evidence and guide recovery. A good responder balances speed with rigour.
Digital Forensic Investigator
Bridges technical findings and legal requirements, often in collaboration with law enforcement or legal teams. Clarity and documentation are key.
Across these roles, the core skills are consistent: solid knowledge of systems and networks, structured analysis, clear writing and a strong ethical compass.
The Final Byte
Cyber forensics underpins modern cyber security. It explains what happened, proves what matters and points to what to fix. For organisations, building forensic capability into your security program is now a must, not a nice to have. It shortens recovery, strengthens compliance and improves the way you prevent, detect and respond.
As our digital footprint grows, the demand for people who can read and interpret that footprint will grow with it. If you are building a career, there is meaningful work here. If you are leading a business, investing in forensic readiness is one of the smartest risk decisions you can make.





