In this article
The healthcare sector has gone digital to improve patient outcomes and operational efficiency.
Electronic health records, telehealth platforms and connected medical devices have transformed healthcare across Australia. But this digitalisation has also created a bigger attack surface that cybercriminals are actively exploiting.
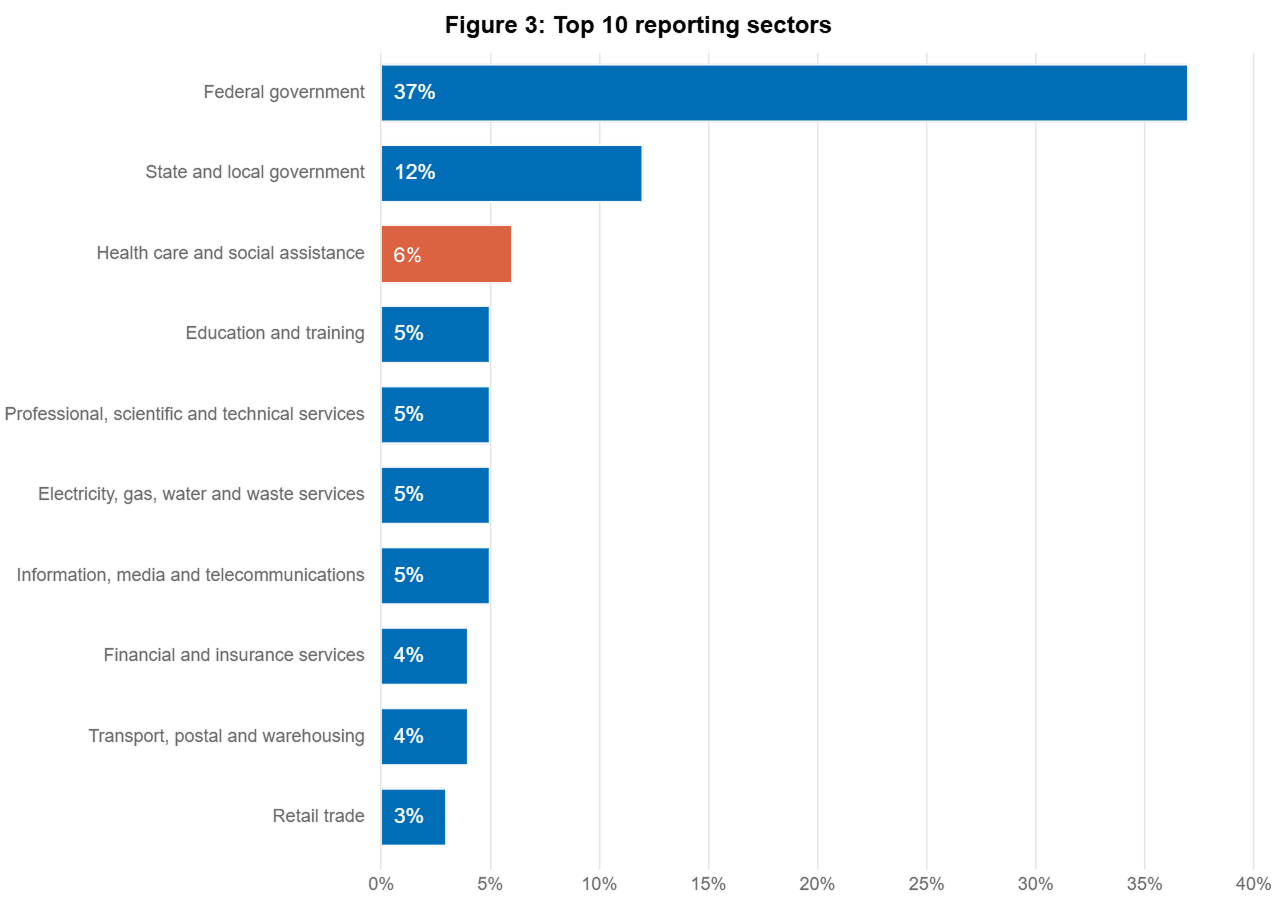
Healthcare organisations are a prime target for threat actors because of the sensitive patient data they hold and their need for continuous operations. According to the Australian Cyber Security Centre’s (ACSC) Annual Cyber Threat Report 2023-2024, healthcare rose to become the most targeted non-government sector in the economy.
The impact of cyber attacks on healthcare goes beyond financial losses and regulatory penalties. Patient safety, clinical care and essential services can be compromised when systems are breached.
The healthcare industry’s combination of valuable data, critical infrastructure and operational intimacy makes cyber security not just an IT issue but a core part of healthcare service delivery and patient safety.
Recent Cyber Attacks on Australian Healthcare Organisations
In recent years we have seen several significant cyber incidents affecting Australian healthcare providers:
Medibank Breach (2022): One of Australia’s largest health insurers was hit by a massive data breach affecting 9.7 million current and former customers. The attack exposed sensitive patient data, including medical claims information and personally identifiable information. The breach resulted in widespread data theft with cybercriminals publishing stolen health records on the dark web.
Eastern Health Ransomware (2021): A Victorian healthcare network was forced to cancel multiple surgeries and procedures after a ransomware attack hit their systems. The attack affected multiple hospitals and disrupted service for weeks.
St Vincent’s Health Australia (2023): One of Australia’s largest healthcare networks experienced a cyber incident that impacted several of their facilities across multiple states. The incident resulted in the theft of sensitive patient and staff data, including names, contact details, Medicare numbers, dates of birth, and medical information.
For employees, tax file numbers, bank details, and superannuation information were also compromised. While hospital operations remained largely unaffected, the organisation had to implement additional security measures and establish support services for affected individuals.
Australian Clinical Labs (2023): In 2023 Australian Clinical Labs confirmed a significant data breach affecting approximately 223,000 patients. The breach exposed sensitive medical information including test results, Medicare numbers and health conditions. The incident occurred through their Medlab Pathology subsidiary and resulted in regulatory investigation and subsequent lawsuit by the OAIC.
These incidents show Australian healthcare organisations are under persistent and evolving cyber threats that can cause significant operational disruption and data compromise. The OAIC plays a key role in monitoring and compliance with the Notifiable Data Breaches (NDB) scheme in the healthcare sector.
Vulnerable Surfaces in Healthcare
The Australian healthcare sector is a unique cyber security challenge due to its mix of technology, operations and regulatory environment. Unlike many other industries, healthcare organisations need to balance the competing demands of data availability for clinical care with protecting sensitive patient information.
This balancing act creates specific attack surfaces that cybercriminals target. The Australian Digital Health Agency (ADHA) has identified several critical attack surfaces that require more than standard enterprise security.
These vulnerabilities have been highlighted in recent times by the sector’s rapid digital transformation, accelerated by the COVID-19 pandemic, which has expanded telehealth services and remote patient monitoring across Australia.
As healthcare delivery continues to evolve with technology, understanding these sector specific vulnerabilities is key to developing effective cyber security strategies to protect both patient data and critical healthcare services.
Patient Data Protection
- Protected health information (PHI)
- Personally identifiable information (PII)
- Medicare details and financial data
- Mental health records
- Genetic information
- Pathology results and diagnostic imaging
- Medical history and treatment plans
This data is valuable to cybercriminals for identity theft, financial fraud and other malicious activities. Under the Privacy Act 1988 and the Notifiable Data Breaches (NDB) scheme, healthcare providers have significant responsibilities to protect this information.
Internet of Medical Things (IoMT) Devices
The proliferation of connected medical devices creates many challenges:
- Medical IoT devices often run older software that can’t be easily updated
- Many devices were designed with functionality over security
- Devices run on outdated operating systems or firmware
- Network segmentation is often inadequate to isolate vulnerable devices
- Device authentication and access controls are often insufficient
The Australian Digital Health Agency (ADHA) has flagged IoMT security as a major risk for healthcare organisations, with devices ranging from infusion pumps and heart monitors to diagnostic equipment presenting attack surfaces.
Service Continuity Requirements
Healthcare operations can’t afford downtime:
- Patient care depends on continuous access to clinical systems and health records
- Emergency services require uninterrupted comms and data access
- Diagnostic services rely on networked equipment and rapid information sharing
- Medication management systems must be operational to prevent errors
- Patient monitoring depends on functioning digital infrastructure
The criticality of these services makes healthcare organisations more vulnerable to ransomware and other attacks that disrupt operations, as service restoration becomes an urgent priority that may pressure organisations into paying ransoms.
Common Attacks on Australian Healthcare
According to the ACSC’s Annual Cyber Threat Report 2023-2024, the most common attacks on Australian healthcare organisations are:
Ransomware
Ransomware is still one of the biggest threats to the healthcare sector. These attacks encrypt critical systems and data and demand payment for release. The ACSC reports 121 ransomware incidents in FY 23/24 accounting for 11% of total reported incidents.
Critical healthcare infrastructure is targeted, with attackers hitting hospital networks, electronic medical record systems and diagnostic equipment.
Australian healthcare providers often face the difficult decision of whether to pay ransoms to restore patient services, despite government advice not to. A new trend is emerging where cybercriminals are stealing patient data and threatening to publish it unless a ransom is paid. Unlike traditional ransomware which focuses on encrypting systems, these attacks target data confidentiality.
To be clear, the ASD advises against paying extortion demands, as payment does not guarantee compliance, further leaking to 3rd party sources online or that the victims data is even recoverable. Ultimately, discouraging the proliferation of the cyber crime business model is the best long-term mitigation.
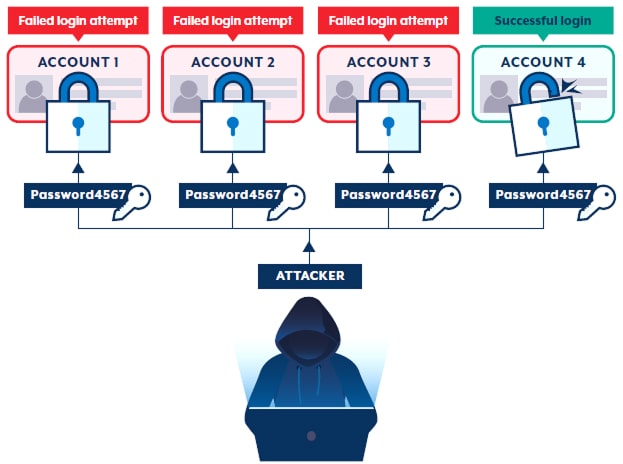
Password Spraying
Unlike traditional brute force attacks that try many passwords against a single account, password spraying tries a small number of common passwords against many accounts.
Healthcare providers are particularly vulnerable to this attack because:
- Many user accounts across multiple systems
- Clinical staff prioritising convenience over security
- Common use of easily guessable passwords related to medical terminology
- Inconsistent multi-factor authentication
- Legacy systems with weak password policies
These attacks target externally facing applications like email portals, telehealth platforms and administrative interfaces. Threat actors target healthcare administrative credentials as an initial access vector, with successful compromises often leading to more serious breaches including ransomware deployment.
Password spraying attacks often occur during off-hours and weekends when security monitoring may be reduced, so 24/7 security operations or automated detection systems are necessary.
Phishing and Social Engineering
Healthcare staff are still vulnerable to sophisticated phishing attacks. The ACSC found 74% of all reported cybercrimes and 55% of loss value originated with a phishing email in 23/24. With clinical and administrative staff the most frequent targets.
These attacks often use healthcare-specific themes such as:
- Messages from medical equipment vendors
- Fake patient record access requests
- Impersonation of pharmaceutical suppliers
- COVID-19 and other health emergency-themed lures
- Fake Medicare or health insurance communications
Healthcare phishing prevention requires ongoing security awareness training for all staff who have access to sensitive systems and data.
Supply Chain Compromise
The interconnectedness of healthcare supply chains poses a big risk.
Healthcare organisations connect with many external parties including:
- Medical device manufacturers
- Pharmaceutical suppliers
- Pathology services
- Electronic health record vendors
- Telehealth platform providers
- Billing and claims processing services
Each of these connections is an entry point for an attacker if not secured.
Threat actors are increasingly targeting smaller vendors with weaker security as an indirect way to get into larger healthcare networks. These “island hopping” attacks allow them to bypass the security of well-protected healthcare organisations by exploiting the trusted connections with their less secure suppliers.
Healthcare software supply chains are also a target, with several cases of compromised software updates or development environments that then affected multiple healthcare providers at once. This amplification effect makes supply chain attacks very attractive to advanced threat actors looking to maximise impact.
Australian Cyber Data Policy & Regulation
Healthcare organisations in Australia must navigate a complex regulatory landscape governing data protection and privacy. Multiple frameworks managed by the Office of the Australian Information Commissioner (OAIC) and the Australian Digital Health Agency (ADHA) establish requirements for securing health information and reporting breaches.
Understanding these regulatory obligations is essential for Australian healthcare providers as they develop cyber security strategies that protect patient data while maintaining compliance with national standards.
Privacy Act 1988 and Australian Privacy Principles (APPs)
The Privacy Act sets out the basic requirements for handling personal information, with healthcare data receiving special protection as “sensitive information”. The Australian Privacy Principles provide guidance on:
- How health information can be collected and used
- Consent for data sharing
- Security requirements for data protection
- Access to health information by individuals
- Disclosure and transparency requirements
All healthcare providers, big or small, are covered by the Privacy Act if they handle health information.
Notifiable Data Breaches (NDB) Scheme
Introduced in 2018, the NDB scheme requires healthcare organisations to notify affected individuals and the Office of the Australian Information Commissioner (OAIC) when data breaches occur that are likely to result in serious harm.
The healthcare sector reports the most notifiable breaches across all industries in Australia, showing the sector’s vulnerability and its compliance challenges.
My Health Records Act 2012
This legislation sets out specific security and access requirements for organisations accessing the national My Health Record system. Healthcare providers must have and enforce a written security and access policy under Rule 42 of the My Health Records Rule to register and use the system.
Essential Eight Framework
While not healthcare-specific, the ACSC’s Essential Eight framework provides baseline mitigation strategies that the healthcare sector is adopting. The framework covers:
- Application control
- Patch applications
- Configure Microsoft Office macro settings
- User application hardening
- Restrict administrative privileges
- Patch operating systems
- Multi-factor authentication
- Regular backups
Healthcare security compliance is increasingly aligning with these controls as they are the minimum security standard for Australian healthcare organisations.
Healthcare Cyber Maturity
Challenges
Australian healthcare organisations face several unique challenges in building cyber security:
Legacy Systems and Infrastructure
Many healthcare facilities have outdated clinical systems that lack modern security features. Public hospitals, particularly in regional areas, have medical devices and information systems that cannot be easily updated or replaced due to budget constraints and operational dependencies.
Resource Limitations
Healthcare organisations prioritise clinical spend over cyber security investments. Limited IT budgets and lack of security staff create significant gaps in healthcare cyber defence. The Australian digital health landscape reflects this imbalance, with many providers without dedicated security teams.
Complex Digital Ecosystem
The average Australian hospital network has hundreds of applications, systems and connected devices. The complex ecosystem creates integration challenges and expands the attack surface. Healthcare identity management becomes more challenging with staff requiring varying levels of access to multiple systems.
Compliance vs. Security
Meeting regulatory requirements doesn’t mean strong security postures. Many healthcare organisations focus on minimum compliance rather than security strategies. The gap between compliance and security creates vulnerabilities that attackers exploit.
Strategies and Solutions
Implement a Security Framework
Australian healthcare organisations should develop security frameworks that go beyond compliance requirements. A cyber risk assessment can help identify vulnerabilities specific to your healthcare environment and guide the implementation of appropriate controls:
Adopt the ACSC’s Essential Eight
- Implement healthcare-specific security for clinical systems
- Develop incident response plans for various cyber scenarios
- Establish data classification for health information
- Network segmentation for clinical systems and medical IoT devices
Invest in Staff Security Awareness
Human error is the primary vector for successful attacks:
- Develop healthcare-specific training programs
- Run regular phishing simulations for healthcare
- Clear procedures for reporting suspicious activity
- Role-based training for clinical vs. administrative staff
- Positive security culture that prioritises patient safety
Healthcare staff can join the Australia-wide Cyber Champions Network to collaborate and share knowledge.
Secure Medical Devices
Medical IoT devices require dedicated security:
- Network monitoring for abnormal device behaviour
- Device inventory and risk assessment
- Network segmentation for vulnerable devices
- Access controls for device management
- Patch management for medical devices
Zero Trust Architecture
The network perimeter is dissolving in healthcare:
- Multi-factor authentication for all system access
- Principle of least privilege for user and system accounts
- Continuously verify and validate all connections and access requests
- Endpoint protection on all devices
- Monitor and log all access to sensitive systems and data
Third-Party Risk Management
Healthcare organisations rely on external vendors and service providers:
- Vendor security assessment process
- Security requirements in all contracts
- Regular review of third-party access and privileges
- Monitor vendor security performance and compliance
- Incident response plans for third-party scenarios
The Future of Healthcare Cyber Security in Australia
The Australian healthcare cyber landscape is changing fast. Partner with a medical IT services provider to stay ahead of the threats and adapt your security strategy:
Artificial Intelligence
- Threat actors using AI to create more complex attacks
- Defensive AI to detect anomalies
- Machine learning to improve threat detection
- Automated response to reduce incident response time
- AI-powered analytics for vulnerability management
Higher Penalties for Security Breaches
- More detailed security controls may be prescribed
- Healthcare specific cyber standards may emerge
- International privacy regulations will converge
- Industry maturity is developing
A More Unified Healthcare Sector Approach
- Threat intelligence is being shared
- Industry-wide security initiatives are gaining traction
- Public-private partnerships are strengthening security
- Standardised security is being developed
- Shared security is helping smaller providers
Protecting the Lifeblood of Healthcare
Cyber security in Australian healthcare has evolved from a reactive footing to a strong focus on protecting patient care systems and maintaining business continuity. The sector is a natural target for cyber criminals with complex systems, operational requirements and sensitive data, requiring a strong cyber security posture.
Achieving a mature cyber security posture requires healthcare organisations to balance compliance with security, implement the right technology, training cyber aware staff well and having robust processes for prevention, detection and response.
By addressing the healthcare specific vulnerabilities and adopting a long-term proactive risk-based approach to security, Australian healthcare providers can better protect their patients, operations and reputation from cyber attacks. Need a pro-active cyber security partner to help get you there? Contact us.