In this article
Let’s talk about something that’s been a hot topic in our industry: multi-factor authentication (MFA).
I get it—you might be rolling your eyes thinking, “Not another security hurdle to jump over!” But hear me out. From my years of experience working with businesses like yours, I’ve seen firsthand how MFA can transform your security posture.
By incorporating biometric data and hardware tokens into your MFA solutions, you can create a robust and seamless system that considers mobile devices, user locations, and behaviour patterns. In this post, we’ll break down the importance of MFA, guide you through effective implementation strategies, and address common obstacles.
So, pour yourself a coffee, and let’s dive in!
Understanding MFA
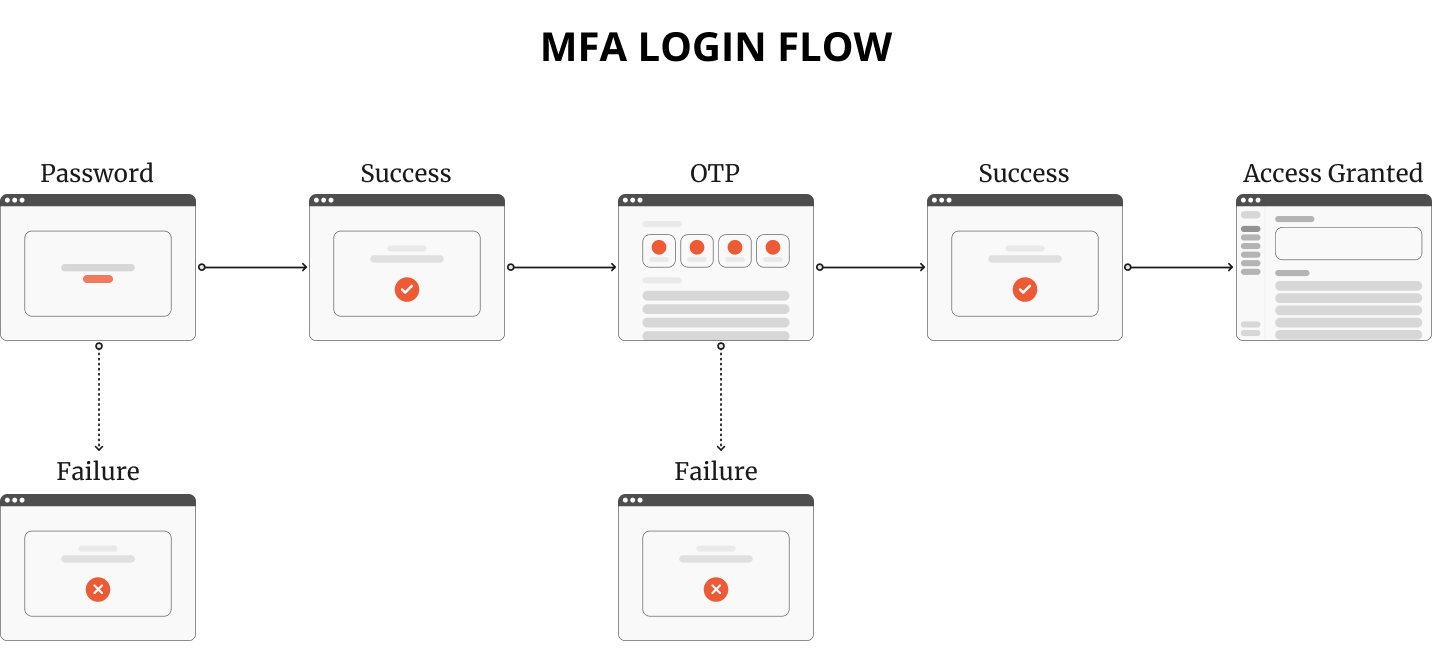
So, what exactly is MFA? Think of it as a bouncer for your digital assets. Instead of just asking for a password (which, let’s face it, could be your dog’s name), MFA asks for multiple authentication factors.
Something you know: This could be a password or PIN. Things you have memorised.
Something you have: This might be your smartphone or a special security token. It’s a physical thing you possess.
Something you are: This is the fancy bit—think fingerprints or facial recognition. It’s uniquely you.
MFA aims to verify user identities, which have become the new perimeter for securing networks.
But that’s not all. We can also use contextual factors like location, behaviour, or network information to make MFA even smarter. It’s similar to a security guard who recognises your favourite spots and routines.
Let’s break it down a bit further. When you implement MFA, you’re essentially creating multiple layers of security. Even if one layer is breached, you still have additional layers for protection. An attacker might get past one, but getting through all of them? That’s a whole different ball game.
And here’s something I love about MFA: it’s adaptable. You can adjust the level of security based on the sensitivity of the information being accessed. For example, you might use simple two-factor authentication for accessing company announcements but require three factors for financial data. It’s all about finding the right balance for your organisation’s needs.
Limitations of weak passwords
Now, let’s talk about passwords for a moment. We’ve been using them for decades, and they’ve served us well. But let’s be honest, weak passwords pose significant risks, such as leading to hacking incidents and data breaches, and they stress IT and support teams. (ever get annoyed with a mandatory reset? Imagine how your IT team feels managing it).
We’ve all been guilty of using easy-to-guess passwords or reusing them across multiple accounts. You wouldn’t use the same key for your house, car, and office—if someone gets hold of it, you’re in big trouble.
Here are some of the key limitations of passwords:
- Easy to guess: “123456” and “password” are still among the most common passwords.
- Reused across accounts: If one account is compromised, they’re all at risk.
- Vulnerable to phishing: It’s too easy for users to be tricked into giving away their passwords.
- Difficult to remember: Complex password requirements often lead to users writing them down, which defeats the purpose.
MFA evolved to address these weaknesses and enhance our overall security posture. MFA does not aim to completely replace passwords (although we will discuss passwordless alternatives later); instead, it enhances security by addressing the weaknesses of passwords.
The Value of MFA
Now, you might be wondering, “Is it really worth the hassle?” Let me tell you, the benefits really do pay-off:
Enhanced security
MFA significantly reduces the risk of unauthorised access. It’s like adding multiple locks to your door. Implementing MFA for all user accounts adds an extra layer of protection, preventing unauthorised access and reducing the risk of data breaches.
Even if someone guesses your password, they’d still need your phone or your fingerprint to get in.
Compliance
Many Australian regulations now require strong authentication measures. MFA helps you tick those compliance boxes. It’s not just about avoiding fines; it’s about demonstrating that you take data protection seriously.
Reduced risk of data breaches
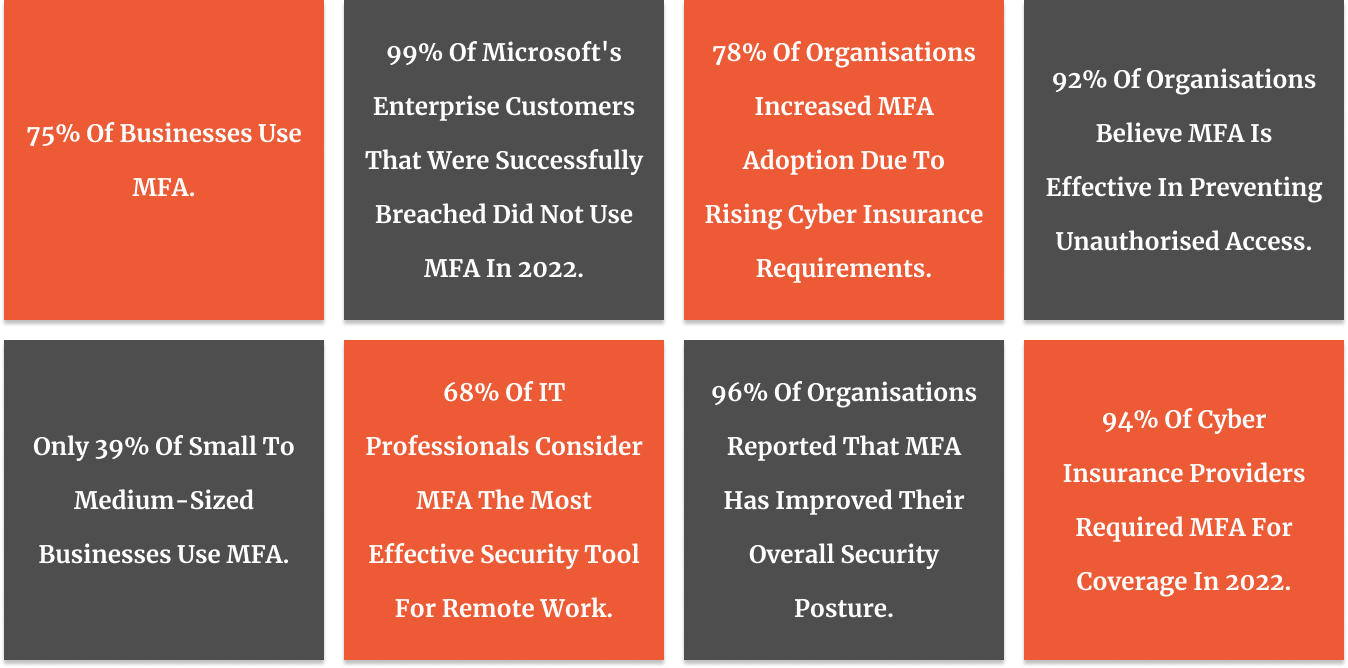
With MFA, you’re making it exponentially harder for the bad guys to get in. Microsoft states that MFA can prevent more than 99.9% of account compromise attempts. That’s a statistic that helps me sleep better at night!
Cost-effective protection
Trust me, implementing MFA is more cost-effective than dealing with a data breach. The average cost of a data breach in Australia is over $3 million. Suddenly, the cost of implementing MFA doesn’t seem so bad, does it?
Improved accountability
MFA ensures that only authorised individuals can access your sensitive information. It’s easier to track who accessed what and when, which is crucial for both security and auditing purposes.
But it’s not just about the technical benefits. Implementing MFA sends a message to your customers, partners, and employees that you take security seriously. Implementing MFA enhances trust and confidence in your brand. In today’s digital world, that’s worth its weight in gold.
Top 10 Best Practices for Implementing MFA
Alright, let’s get into the nitty-gritty. Here are my top 10 tips for implementing multi factor authentication in 2024:
- Leverage context for adaptive MFA:Use information about user behaviour, location, and devices to adjust your security measures dynamically. For example, if a user is logging in from a new location or at an unusual time, you might require additional authentication factors.
- Select a standards-based approach: Choose MFA solutions that play nicely with industry standards. It’ll save you headaches down the road when you need to integrate with other systems or upgrade your security infrastructure.
- Combine MFA with complementary identity security tools: Think of MFA as part of your overall security ecosystem. Integrate it with tools like Single Sign-On (SSO) and Identity and Access Management (IAM) for a comprehensive security strategy.
- Regularly re-evaluate MFA effectiveness: The security landscape is always changing. Make sure your MFA strategy keeps up. This might involve penetration testing, reviewing authentication logs, or staying informed about new vulnerabilities.
- Provide a variety of authentication factors: Give your users options. Some might prefer biometrics; others might like push notifications. The more options you provide, the more likely users are to embrace MFA.
- Use Single Sign-On (SSO) with MFA: Combine these for both security and convenience. SSO reduces the number of passwords users need to remember, while MFA ensures that the single point of access is well protected.
- Consider going passwordless: It might sound radical, but it can actually boost both security and the user experience. Passwordless methods, like biometrics or security keys, can be more secure and easier to use than traditional passwords.
- Educate users on MFA importance and usage: Help your team understand why MFA matters and how to use it effectively. This isn’t just about sending out an email; consider hosting training sessions, creating video tutorials, or setting up a help desk specifically for MFA-related queries.
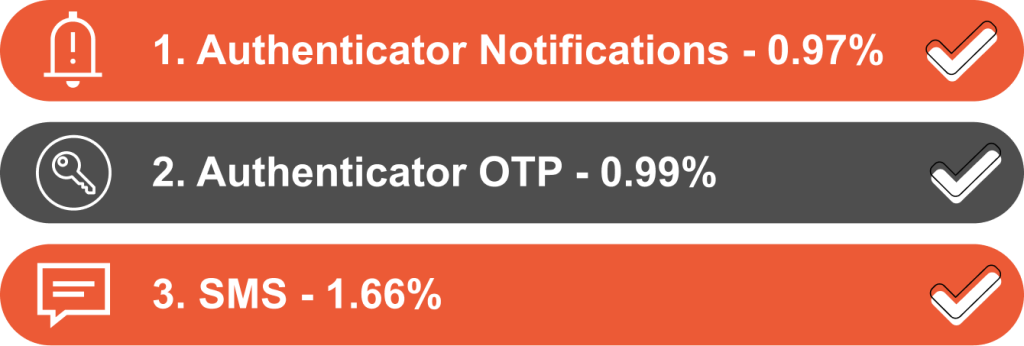
- Think twice about using SMS for OTP: SMS isn’t as secure as we once thought. Consider more robust alternatives, like authenticator apps or push notifications. If you do use SMS, make sure you have additional security measures in place.
- Plan for lost or stolen MFA devices: Have a clear process in place for when things go wrong. This might include backup authentication methods, a streamlined process for revoking access to lost devices, and a way to quickly issue new authentication factors.
Remember, implementing these IT security best practices isn’t a one-time thing. It’s an ongoing process that requires regular review and adjustment. But trust me, the effort is worth it.
Common Adaptive MFA Implementation Challenges
I’ll be straight with you: implementing MFA isn’t always smooth sailing. Here are some challenges you might face and how to overcome them:
User resistance
Change can be hard, and some users might see MFA as an inconvenience. The key here is clear communication and education. Explain why MFA is important, how it protects both the company and the individual, and provide ample support during the transition.
Additionally, provide detailed guidance on user verification best practices, including recommendations for different verification channels, authentication preferences, and backup methods.
Balancing security and user experience
It’s a tightrope walk, but finding the right balance is crucial. Start with less intrusive MFA methods and gradually increase security as users become more comfortable. Regularly gather feedback and be prepared to make adjustments.
Handling lost or stolen MFA devices
This is bound to happen at some point. Have a clear, simple process for what to do when it does. This might include a dedicated helpline, a self-service portal for resetting authentication factors, or a backup authentication method.
Accommodating special cases
Sometimes, a standard MFA might not work for everyone. Be prepared to make exceptions when necessary, but make sure these exceptions are documented and regularly reviewed.
Integration with legacy systems
Some of your older systems might not play nice with MFA. You might need to use middleware solutions or consider updating these systems. It’s a challenge, but it’s also an opportunity to modernise your IT infrastructure.
Cost concerns
While MFA is cost-effective in the long run, the initial implementation can be expensive, especially for smaller businesses. Look for scalable solutions that can grow with your business, and consider the cost savings from preventing breaches when making your case to management.
Keep in mind that encountering these challenges is a common part of the process. Every business faces them when implementing MFA. The key is to anticipate them and have a plan in place to address them.
MFA and Regulatory Compliance in Australia
As Aussie businesses, we’ve got some specific regulations to consider:
Privacy Act
The Privacy Act requires organisations to take reasonable steps to protect personal information. MFA is increasingly seen as one of these “reasonable steps.” Implementing MFA can help you demonstrate that you’re taking proactive measures to protect data.
Notifiable Data Breaches (NDB) Scheme
This scheme requires organisations to notify individuals and the Office of the Australian Information Commissioner (OAIC) about data breaches that are likely to result in serious harm. MFA can be a powerful tool for preventing these kinds of breaches in the first place.
APRA standards
For those in financial services, the Australian Prudential Regulation Authority (APRA) specifically calls out MFA as a critical control in its Prudential Standard CPS 234. Remote Authentication Dial-in User Service (RADIUS) is a standards-based MFA solution that provides centralised authentication, authorisation and accounting management for users connecting to and relying on a network service. If you’re in this industry, implementing MFA isn’t just good practice; it’s a regulatory requirement.
Essential Eight
Although not a specific regulation, the Australian Signals Directorate’s Essential Eight Maturity Model suggests using MFA as a critical strategy to reduce cyber security risks. It’s a good framework to follow, regardless of your industry.
Remember the Medibank breach in October 2022? That’s a stark reminder of what can happen when our defences aren’t up-to-date. The breach affected millions of customers and is estimated to cost the company hundreds of millions of dollars. While we can’t say for certain that MFA would have prevented this breach, it certainly would have made the attackers’ job much harder.
When implementing MFA, make sure you’re documenting your processes and regularly reviewing your compliance. This documentation can be crucial during audits or if you ever need to demonstrate your security measures to regulators.
Measuring the Success of MFA Implementation
Implementing MFA is fantastic, but how can you measure its effectiveness? Here are some key performance indicators (KPIs) to keep an eye on:
Adoption rate:
Track the percentage of user accounts that have successfully enrolled in MFA. Aim for 100% adoption across all user accounts, but don’t be discouraged if it takes time to get there.
Authentication success rate
Monitor the percentage of successful MFA authentications. A high success rate indicates that users are comfortable with the system and that it’s functioning correctly.
Security incident reduction
Measure the decrease in security incidents after MFA implementation. This could include unauthorised access attempts, account takeovers, or data breaches.
User satisfaction
Gather feedback to assess the user experience and identify areas for improvement. This could be done through surveys or by monitoring help desk tickets related to MFA.
Time to authenticate
Measure the average time it takes for users to complete the authentication process. While security is paramount, excessive authentication times can impact productivity.
MFA bypass attempts
Monitor and investigate any attempts to bypass MFA. This can help identify potential vulnerabilities or areas where user education may be needed.
Continuously improving your MFA strategy
Implementing MFA isn’t a “set it and forget it” kind of deal. Here’s how you can keep improving:
Conduct regular security audits & assessments
This should include penetration testing to identify any weaknesses in your MFA implementation. Emphasise the importance of securing user identities, as they are the new perimeter for network security.
Gather and act on user feedback
Proactively seek input from users to pinpoint pain points and areas for enhancement. Remember, your users are on the front lines; their insights are invaluable.
Stay informed about emerging threats & MFA technologies
The cyber security landscape is constantly evolving. Keep abreast of new threats and innovations in MFA technology to ensure your strategy remains effective.
Review and update your policies regularly. As your business grows and changes, your MFA policies may need to evolve too. Ensure that you regularly review and update your MFA policies to maintain strong security measures.
Cybercriminals Hate This One Trick: Implement MFA!
We’ve covered a lot of ground here.
But it’s worth re-capping MFA is a crucial step in protecting your Australian business from cyber threats.
Implementing multi factor authentication and securing user identities are essential for strengthening network protection, it was built to enhance traditional passwords. It’s not always easy, but the peace of mind it brings is priceless.
But don’t think you’re not alone in this journey. At TechBrain, we specialise in tailoring MFA strategies for businesses just like yours. Our cyber security consultants can help you navigate the complexities of MFA implementation, ensuring your business stays secure without sacrificing usability.
We can help you choose the right MFA solution, integrate it with your existing systems, train your staff and ensure you’re meeting all relevant Australian compliance requirements. Plus, we’ll be there to support you as your needs evolve and new challenges arise.
Are you ready to take your security to the next level? Let’s chat about how we can make MFA work for you. Your future self (and your IT team) will thank you!