In this article
Today’s business leaders understand the critical role that technology plays in their organisation’s success. But with great technological power comes great responsibility – and significant risk. The constant threat of cyber attacks, the challenge of staying compliant with ever-changing regulations, and the need to protect your company’s most valuable assets – its data and reputation – can keep even the most seasoned executives up at night.
I’ve seen firsthand the impact of cyber incidents on businesses – from financial losses and operational disruptions to damaged customer trust and tarnished brand reputations. That’s why I want to talk to you about cyber security maturity – not as a technical issue to be delegated to your IT department, but as a crucial business strategy that demands your attention and leadership.
Whether you’re a CEO looking to safeguard your company’s future, a CFO concerned about the financial implications of a data breach, or a business owner striving to protect what you’ve built, understanding your organisation’s cyber security maturity level is key to making informed decisions and ensuring sustainable growth.
In this article, we’ll demystify cyber security maturity and show you how it can become a powerful tool in your business arsenal. We’ll explore how improving your cyber security maturity can:
- Protect your bottom line
- Enhance your competitive edge
- Ensure business continuity
- Build customer trust and loyalty
- Support your growth and innovation strategies
So, let’s dive in and discover how you can turn cyber security from a necessary expense into a strategic asset for your business.
What is a Cyber Security Maturity Model?
Think of a cyber security maturity model as a comprehensive framework for enhancing your organisation’s digital resilience. It’s not unlike the business maturity models you may be familiar with in areas like operational excellence or customer experience.
At its core, a cyber security maturity model is a tool that helps you understand where your organisation stands in terms of its ability to protect itself against cyber threats and how to systematically improve that position.
These models typically define several levels of maturity:
Initial: Basic security measures are in place, but responses are largely reactive.
Developing: Some standardised processes exist, but there’s room for improvement.
Defined: Well-documented and standardised processes are implemented across the organisation.
Managed: Processes are not only defined but actively monitored, measured, and continuously improved.
Optimising: The organisation is focused on innovation and staying ahead of emerging threats.
Just as you wouldn’t expect your business to leap from a startup to a multinational corporation overnight, you can’t transform your cyber security posture in one giant step. A maturity model helps you assess your current position, set realistic goals, and create a structured plan to reach them.
Why Should Business Leaders Care?
Risk Management: Understanding your maturity level helps you identify and prioritise cyber risks, allowing for more informed decision-making about risk acceptance, mitigation, or transfer.
Resource Allocation: By knowing where you stand, you can more effectively allocate resources – both financial and human – to the areas that will have the greatest impact on your security posture.
Competitive Advantage: In an era where data breaches make headlines, a mature cyber security posture can be a significant differentiator, building trust with customers, partners, and investors.
Regulatory Compliance: Many industries are facing increasing regulatory requirements around data protection. A mature cyber security approach can help ensure compliance and avoid costly penalties.
Business Continuity: Higher levels of cyber security maturity correlate with improved incident response capabilities, minimising downtime and business disruption in the event of an attack.
Strategic Alignment: A maturity model helps align cyber security efforts with broader business objectives, ensuring that security enables rather than hinders growth and innovation.
Remember, improving your cyber security maturity is a journey. It requires ongoing commitment, but the rewards – in terms of risk reduction, operational efficiency, and business resilience – are well worth the investment.
Measuring Cyber Maturity
As a business leader, you’re accustomed to measuring performance across various aspects of your organisation. Cyber security should be no different. But how do you measure something as complex and ever-changing as cyber maturity?
Evaluating and improving your organisation’s cyber security posture is crucial. This involves using models like cyber security maturity models and the NIST Cyber security Framework to conduct baseline assessments and obtain measurable security ratings. Let’s break it down into key areas that align with your business priorities.
Key Assessment Areas
When evaluating your organisation’s cyber maturity, consider these critical business dimensions:
Risk Management and Governance
- How well is cyber risk integrated into your overall enterprise risk management? Utilising a cyber security capability maturity model can help assess and enhance your cyber security capabilities across IT and operational technology assets.
- Is there clear accountability for cyber security at the board and executive levels?
Financial Planning and Investment
- Is your cyber security budget aligned with your risk profile and business objectives?
- How do you measure return on investment for security initiatives?
Operational Resilience
- How quickly can your business recover from a cyber incident?
- Are your critical business processes adequately protected?
Legal and Compliance
- How well-positioned are you to meet current and emerging regulatory requirements?
- Are you prepared to handle the legal implications of a data breach?
Cyber Awareness and Culture
- Is cyber security awareness embedded in your corporate culture?
- How effective are your training programs in reducing human-related security risks?
Vendor Risk Management
- How well do you manage cyber risks in your supply chain and partnerships?
- Are your vendors and partners held to appropriate security standards?
Essential Metrics
While there are countless metrics you could track, here are some essential ones that give you a good overview of your cyber maturity and form the core of most frameworks:
Mean Time to Detect (MTTD): How quickly can you identify a security incident? The lower the number, the better the outcome.
Mean Time to Respond (MTTR): Once detected, how fast can you contain and mitigate the threat? Again, lower is better.
Patch Efficiency: What percentage of your systems are patched within your policy timeframes? Strive to reach as close to 100% as possible.
Security Training Completion Rate: What percentage of your employees have completed and passed your security awareness training?
Incident Rate: The number of security incidents over a given period. Track this over time to see if your defences are improving.
Policy Compliance Rate: How well are your security policies being followed across the organisation?
By focusing on these areas and metrics, you can gain a comprehensive view of your organisation’s cyber maturity without getting lost in technical details. This approach allows you to make informed decisions about risk acceptance, resource allocation, and strategic investments in your company’s digital resilience.
Remember, the goal isn’t to achieve perfect security – which is neither possible nor cost-effective – but to reach a level of maturity that aligns with your risk appetite and business objectives. Adopting a solid framework for regular assessment of these areas will help you track progress and adjust your strategy as your business evolves and the threat landscape changes.
Certifiable Cyber Security Maturity Models
Taking further steps to certifiable frameworks, there are a number of widely recognised cyber security maturity models that can guide your cyber security journey. These structured frameworks help organisations evaluate and improve your organisation’s cyber security posture management processes.
Established models such as NIST CSF, CIS, and CMMC emphasise the importance of selecting the right framework based on an organisation’s specific needs to effectively manage risk and bolster defences against cyber threats.
NIST Cyber Security Framework
The National Institute of Standards and Technology (NIST) Cyber Security Framework provides a flexible and risk-based approach to improving cyber security. It focuses on five core functions: identify, protect, detect, respond, and recover.
Business Value:
- Provides a common language for communicating about security risks across your organisation and with stakeholders
- Helps align cyber security efforts with business objectives and risk management strategies
- Offers a flexible approach that can be tailored to businesses of all sizes and industries
- Useful for businesses operating internationally or working with U.S. partners
- Enhances your ability to identify, protect, detect, respond to, and recover from cyber incidents by incorporating structured frameworks like the Cyber security Maturity Model Certification (CMMC), which aligns with established guidelines such as NIST and addresses modern cyber security threats
ISO 27001 ISMS
The International Organisation for Standardisation’s Information Security Management System (ISMS) standard provides a systematic approach to managing sensitive company information. It’s widely recognised as the gold standard globally.
Business Value:
- Demonstrates to clients, partners, and regulators that you take information security seriously by adhering to comprehensive cyber security frameworks and best practices, including internet security measures
- Can provide a competitive edge, especially in industries where data protection is crucial
- Helps integrate security processes with overall business processes
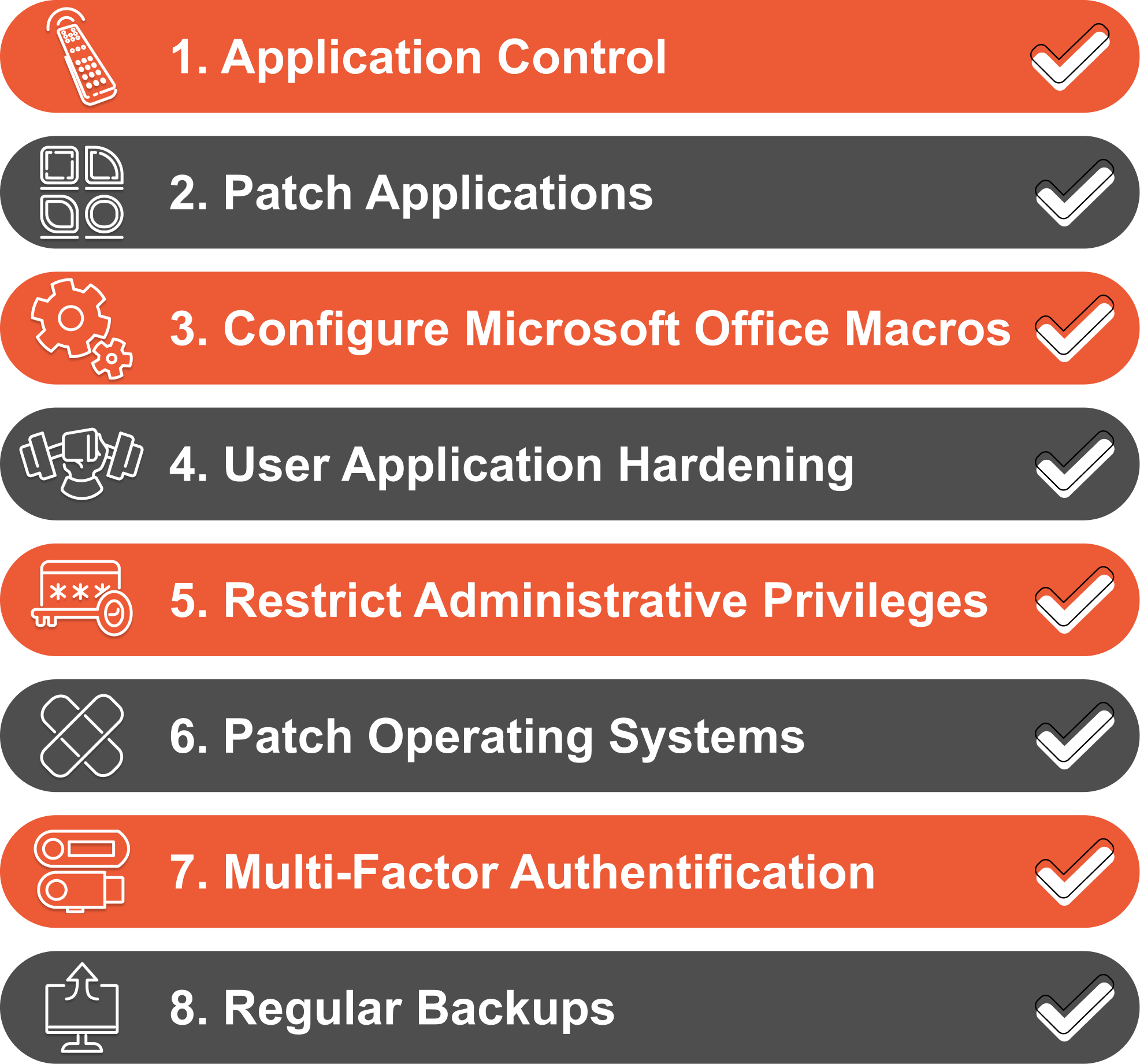
ACSC Essential 8
The Australian Cyber Security Centre’s Essential 8 Maturity Model focuses on eight crucial mitigation strategies. It’s particularly relevant for Australian organisations and defines three maturity levels for each strategy.
Business Value:
- Provides a clear roadmap for improving your most critical security controls and enhancing energy security by safeguarding critical infrastructure against potential cyber threats
- Helps prioritise security investments for maximum impact
- Aligns with Australian government recommendations, which can be beneficial for government contracts or partnerships
COBIT (Control Objectives for Information and Related Technologies)
COBIT is a framework for the governance and management of enterprise IT. While broader than just cyber security, it includes important security-related processes and can help align IT with business objectives. COBIT also emphasises the importance of risk management and compliance.
Business Value:
- Bridges the gap between technical IT issues and business risks, making it easier for non-technical leaders to understand and manage IT-related risks
- Helps align IT and security strategies with overall business goals
- Provides a comprehensive approach to IT governance, which can improve overall operational efficiency
- Enhances decision-making around IT investments and resource allocation
- Can improve stakeholder confidence in your use of IT and management of associated risks
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is crucial for any organisation handling credit card information. While not Australia-specific, it’s a critical standard for many data driven Australian businesses in finance, healthcare, and government services.
Business Value:
- Essential for maintaining the ability to process credit card payments, which is critical for many businesses
- Helps protect against data breaches, which can have severe financial and reputational consequences
- Can enhance customer trust by demonstrating commitment to protecting their financial information
- Provides a clear set of security controls, which can be beneficial even for businesses that don’t process credit cards but handle sensitive data
- Compliance can sometimes lead to reduced transaction fees from payment processors
APRA CPS 234
The Australian Prudential Regulation Authority’s CPS 234 is specific to financial institutions. It sets out requirements for information security, including the need to maintain an information security capability commensurate with the size and extent of threats to information assets.
Business Value:
- Essential for compliance in the financial sector
- Helps manage information security risks in proportion to the potential vulnerabilities and threats
- Can boost confidence among customers and investors in your ability to protect financial data
Adopting a Continuous Improvement Approach
Here’s a hard truth: there’s no finish line in cyber security. The threat landscape is constantly evolving, and so must our defences. That’s why adopting a continuous improvement approach is crucial.
Regular Assessment: Periodically evaluate your current security posture. This isn’t just a technical exercise; it should involve stakeholders from across the business, including IT, legal, and operational teams, to get a holistic view.
Goal Setting: Based on your assessment, set realistic, measurable goals for improvement. These should align with your business objectives and risk tolerance.
Implementation: Put your plan into action. This might involve deploying new technologies, updating processes, or training staff to mitigate risk.
Measurement: Track your progress using key performance indicators (KPIs). These could include metrics like mean time to detect (MTTD) incidents, percentage of systems patched within policy timeframes, or number of employees who have completed security awareness training.
Review and Adjust: Regularly assess your progress and make necessary adjustments to your strategy. This is also an opportunity to celebrate wins and keep the momentum going.
This approach ensures your security measures evolve with the changing threat landscape.
Getting Started with Building Cyber Maturity
Now that you understand the importance of continuous improvement, you’re probably wondering, “Where do I start?” Don’t worry, we’ve got you covered. Here’s a roadmap to kick off your cyber maturity journey:
- Choose a maturity model that aligns with your industry and objectives. For Australian businesses, the Essential Eight maturity assessment is an excellent starting point. It’s designed specifically for our cyber landscape and provides clear, actionable strategies.
- Conduct an initial self-assessment. Think of it as a health check-up for your cyber defenses. Be honest, it’s the only way to improve!
- Set realistic improvement goals. Remember, just like Rome wasn’t built in a day, top-notch cyber security takes time to develop.
- Develop an action plan to address identified gaps. This is your battle plan against cyber threats.
- Implement changes and monitor progress. It’s not only about implementing changes; it’s about ensuring their effectiveness.
- Regularly reassess and adjust your strategy. The cyber world doesn’t stand still and neither should you.
- Consider getting certified. It’s time to earn your spurs and signal to your clients and stakeholders you mean business.
Remember, improving your cyber security maturity is a journey, not a destination. It requires ongoing commitment and adaptation. But you don’t have to go it alone.
For a comprehensive evaluation of your organisation’s cyber security maturity, consider TechBrain’s TechSure cyber risk assessments. Our expert team can help you identify vulnerabilities, evaluate risks and create a tailored action plan to enhance your security posture.
By understanding and advancing your cyber security maturity level, you’re taking a crucial step in protecting your organisation’s digital assets and building resilience against cyber threats.
After all, we all know the value of a good night’s rest – and nothing helps you sleep better than knowing your cyber defences are up to standard.